Overview
Application Data Protection solution provides centralized configuration and policy management and unified display for all the application connectors on the CipherTrust Manager. Application Data Protection solution supports the following connectors:
DPG
CRDP
The Application Data Protection solution consists of:
Central configuration management
Single pane of glass
Central configuration management
Stores the configurations and policies on the CipherTrust Manger. These configurations are created and managed by the Application Data Protection Administrator. These configurations initializes the client software and initiates crypto operations. To use the centralized configuration, the application connector must be registered on the CipherTrust Manager.
Let's consider a scenario where the user's environment has 10 instances of DPG. Now, the user wants to update the symmetric cache expiry interval for all these nodes. The user will have to manually change every configuration file which is a tedious task. But, with central management in picture, the symmetric cache expiry interval is updated only in the configuration and is reflected on all the instances mapped to that configuration. The central configuration management minimizes the manual intervention.
The main components of Central configuration management are:
Creating application
Generating registration token
Registering client on the CipherTrust Manager
Retrieving client configuration/policies from the CipherTrust Manager and using it for cryptographic operations
How it works
The following diagram shows the basic flow of Application Data Protection solution:
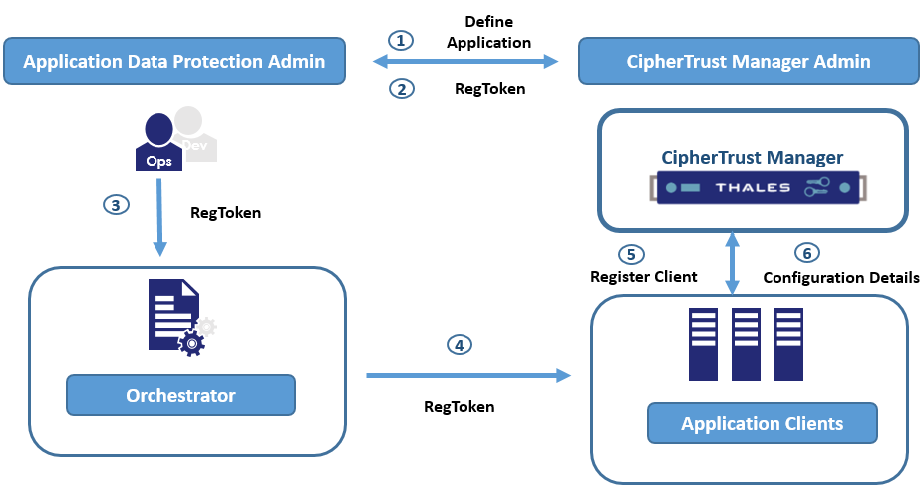
The Application Data Protection Administrator creates an application.
The CipherTrust Administrator sends a Registration Token to the Application Data Protection Administrator.
The Application Data Protection Administrator send the Registration Token to the Orchestrator.
The Orchestrator shares the token details with the client.
Using the token, the client register itself on the CipherTrust Manager.
The CipherTrust Manager shares the client configuration/policies details with the registered client. The client uses the configuration details to perform cryptographic operations.
Single pane of glass
Provides a unified view for all the application connectors that are registered on the CipherTrust Manager. With all the connectors at one place, it becomes easy for the Application Data Protection Administrator to manage and keep track of them. Currently, there is no mechanism for the admins to view the details of a connector. To know more about this topic, refer to Unified Display for Connectors.
User Roles
Application Data Protection has the following users with different responsibilities in administering and using the system.
Application Data Protection Admins
There is a System Defined Group named "Application Data Protection Admins". Users within this group are Application Data Protection Administrators.
A Application Data Protection Administrator is responsible for creating and managing the following resources:
Application Data Protection clients
There is a System Defined Group named "Application Data Protection clients". Application Data Protection users registered with the CipherTrust Manager are part of this group.

