Identity Provider (SafeNet Access Exchange) Setup
Configuring the Identity Provider (for example, SafeNet Access Exchange) requires creating a client in SafeNet Access Exchange.
Perform the following steps to create a client in SafeNet Access Exchange:
-
Log into SafeNet Access Exchange as an administrator.
-
On the administrator console, select your realm (for example, Silverfort).
-
In the left pane, under Manage, click Clients, and in the right pane, click Create client.
-
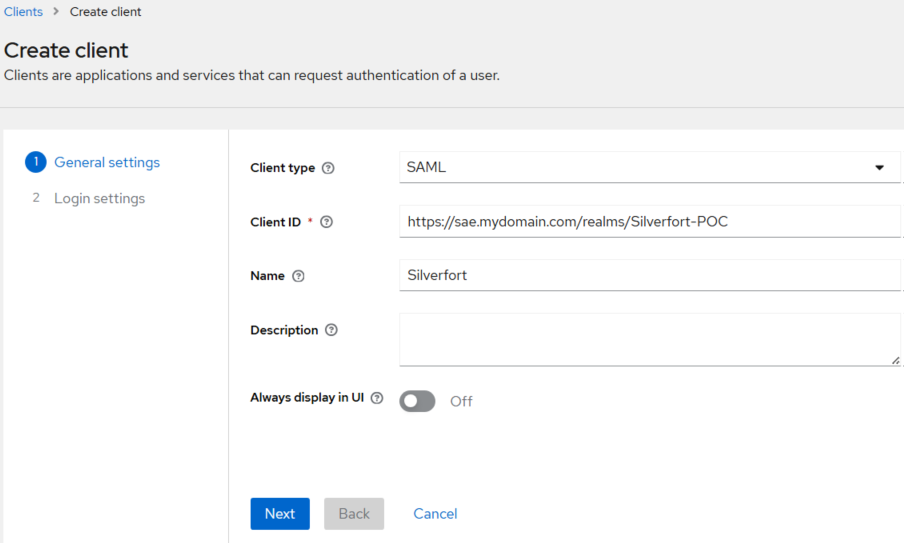
On the General Settings tab, perform the following steps:
-
In the Client type field, select SAML.
-
In the Client ID field, enter a value of your choice (for example, https://sae.mydomain.com/realms/Silverfort-POC).
-
(Optional) In the Name field, enter a name of your choice (for example, Silverfort).
-
Click Next.
-
-
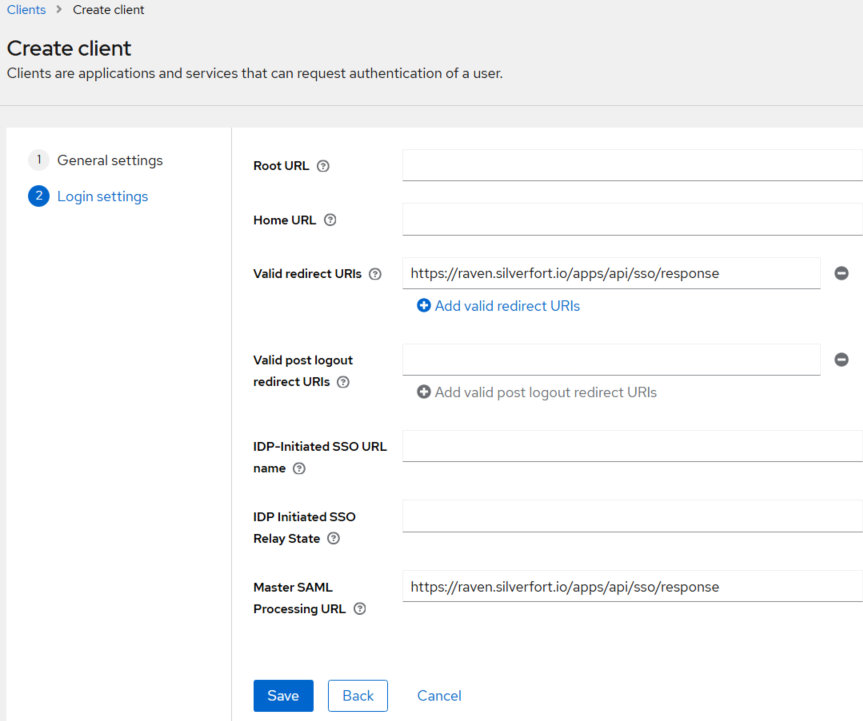
On the Login Settings tab, perform the following steps:
-
In the Valid redirect URIs field, enter the appropriate raven server URL for your region (for example, https://raven.silverfort.io/apps/api/sso/response).
-
In the Master SAML Processing URL field, enter the appropriate raven server URL for your region (for example, https://raven.silverfort.io/apps/api/sso/response).
-
Click Save.
-
-
After creating the client, go to the Settings tab, and configure the following parameters:
-
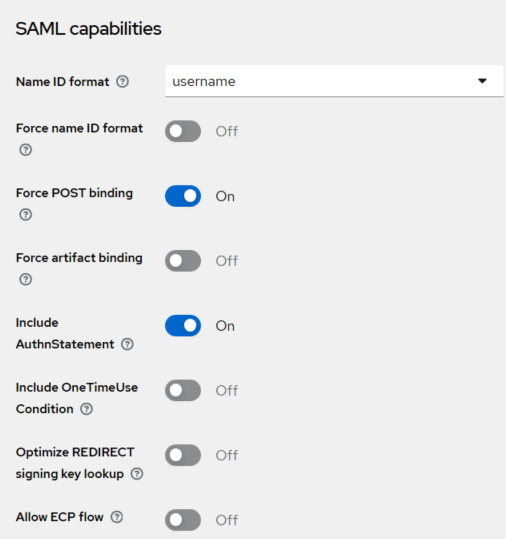
Under SAML Capabilities,
-
In the Name ID format field, select username.
-
Turn On the Force POST binding toggle.
-
Turn On the Include AuthnStatement toggle.
-
-
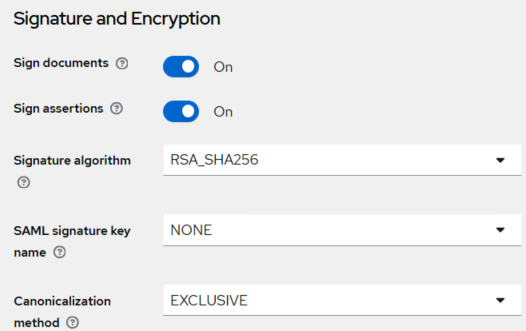
Under Signature and Encryption,
-
Turn On the Sign documents toggle.
-
Turn On the Sign assertions toggle.
-
In the Signature algorithm field, select RSA_SHA256.
-
-
-
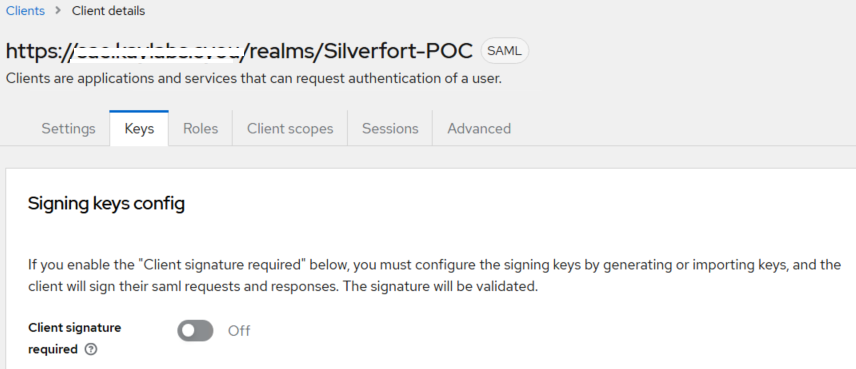
Go to the Keys tab and turn Off the Client Signature required toggle.
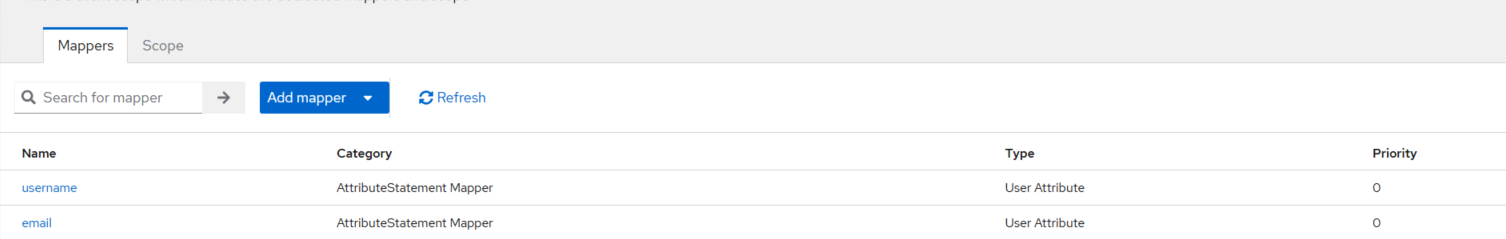
Adding Return Attributes to Meet MFA Requirements
The following types of user return attributes must be included in SafeNet Access Exchange to meet multifactor authentication (MFA) requirements:
-
username
-
email
Perform the following steps to add the return attributes:
-
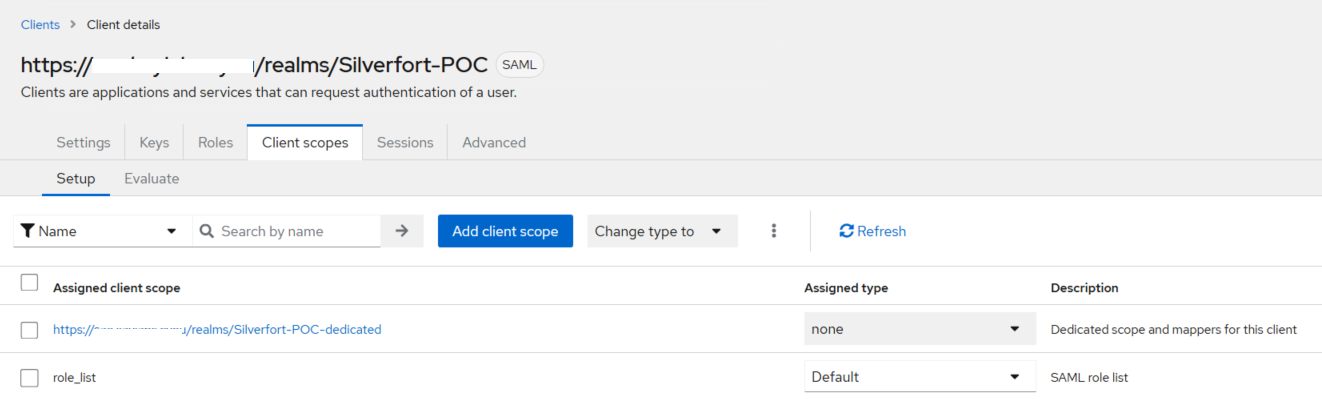
Under Client details, go to the Client scopes tab.
-
Under Assigned client scope, click -dedicated (for example, https://sae.mydomain.com/realms/Silverfort-POC-dedicated).
-
Under Dedicated scopes, on the Mappers tab, click Configure a new Mapper.
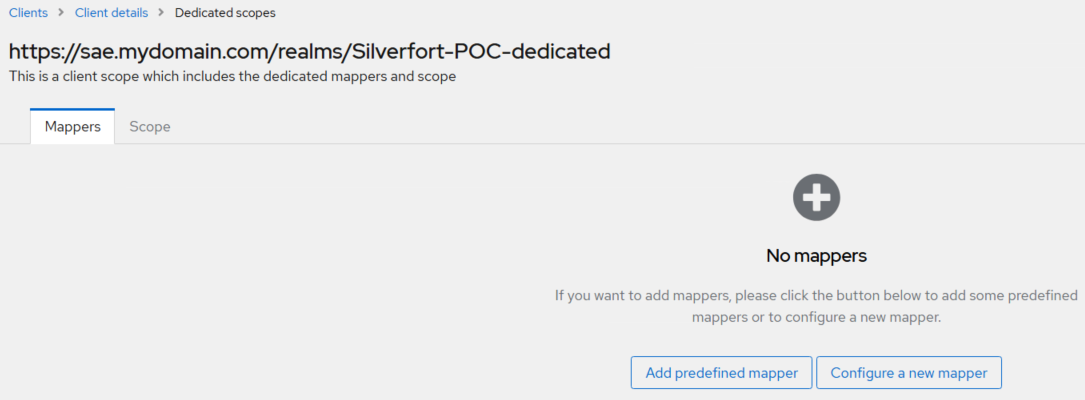
-
Under Configure a new mapper, click User Attribute.
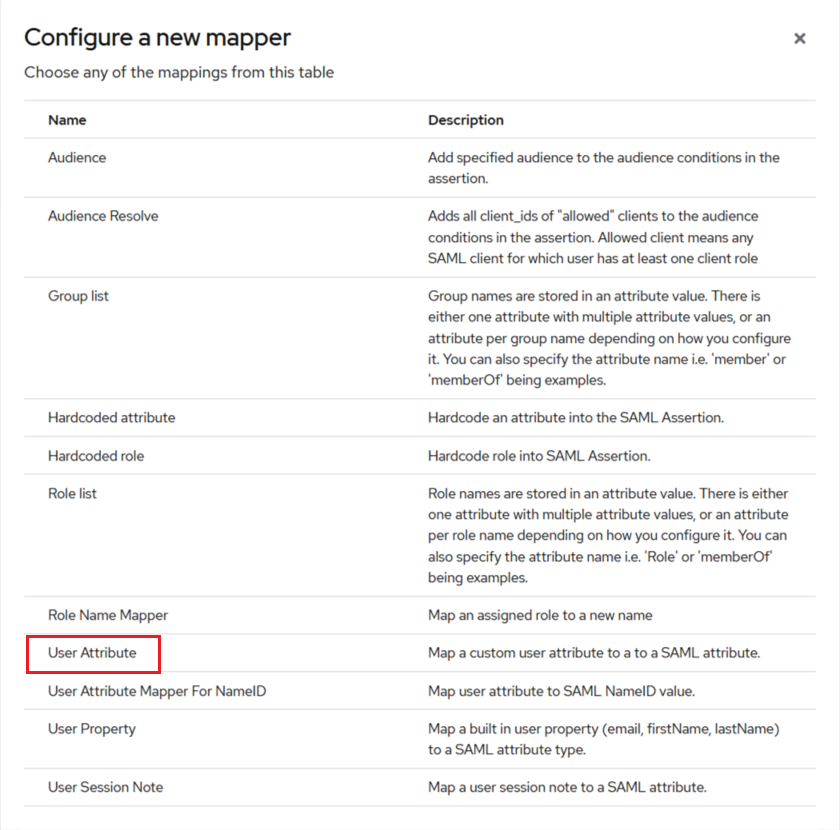
-
Under Add mapper, update the fields' values as per the table below, and click Save.
Field Value Mapper type User Attribute Name username User Attribute email Friendly Name http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name SAML Attribute Name http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name SAML Attribute NameFormat Unspecfied 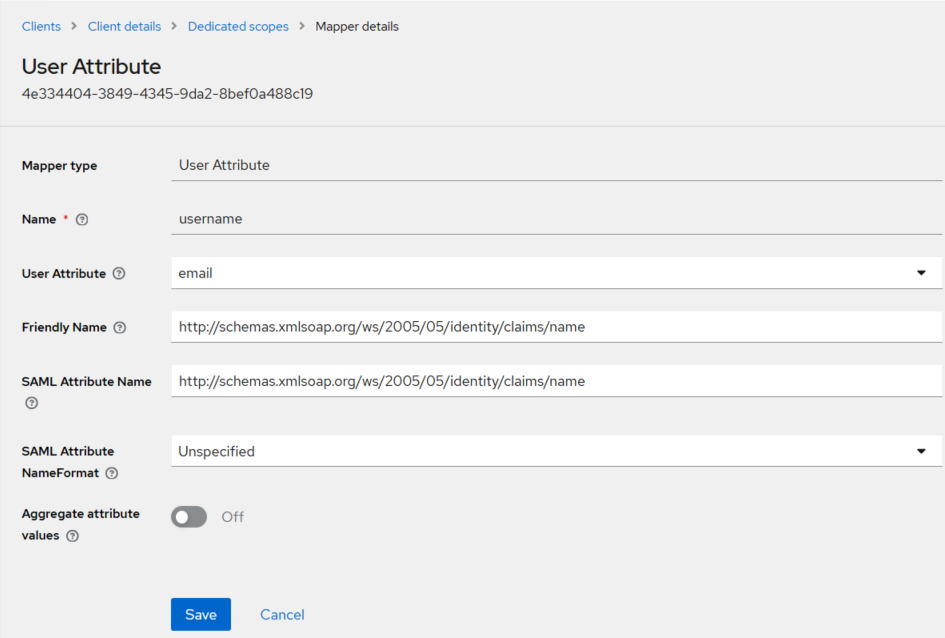
The User Attribute mapper for the username return attribute is successfully added.
-
On the Mappers tab, click Add mapper, and select By configuration.
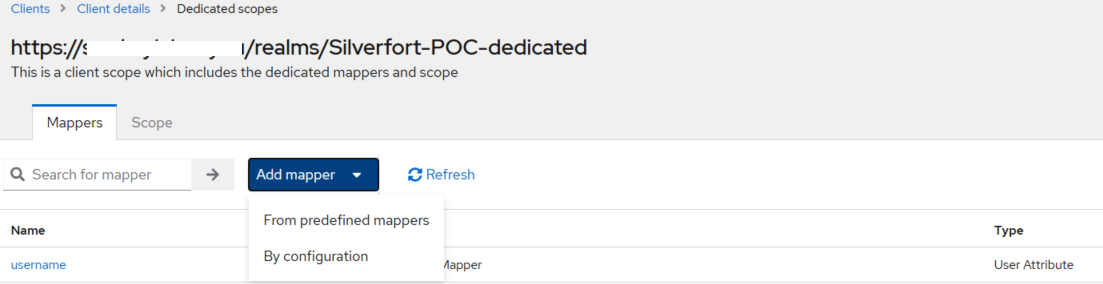
-
Perform the above steps 4 and 5 to add the email user return attribute.
Refer to the table below for the corresponding field values needed to add and configure the email return attribute.
Field Value Mapper type User Attribute Name email User Attribute email Friendly Name http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress SAML Attribute Name http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress SAML Attribute NameFormat Unspecfied