MobilePASS+ token self-provisioning
You can offer your users the option to self-provision a SafeNet MobilePASS+ token. Self-provisioning means that users who don't already have a token can immediately enroll a new token on their own, without using an enrollment email.
The self-provisioning option is displayed on the user portal login screen when an access policy requires a one-time password (OTP) for authentication, but the user doesn't yet have a token. The self-provisioning option is displayed the first time that a user tries to log in to any service that is secured by the identity provider (IdP) and that requires an OTP. After the user enrolls a token, the self-provisioning option is no longer displayed.
Enable MobilePASS+ self-provisioning
To enable groups to self-provision SafeNet MobilePASS+ tokens, see Self-provisioning rules for groups.
Select the target platforms and push notifications
You can select the platforms on which users can enroll MobilePASS+ tokens. The platform is the combination of operating system and device type, such as Android mobile devices.
The target platforms that you select determine which targets are presented to users during MobilePASS+ token self-enrollment.
You can also control the availability of push based on the operating system and device type. For example, you can enable push on mobile devices but not on desktop devices, such as Windows 10, due to the complexity of push in a desktop environment.
-
On the STA Token Management console, select Policies > Token Policies > Software Token & Push OTP Settings.
-
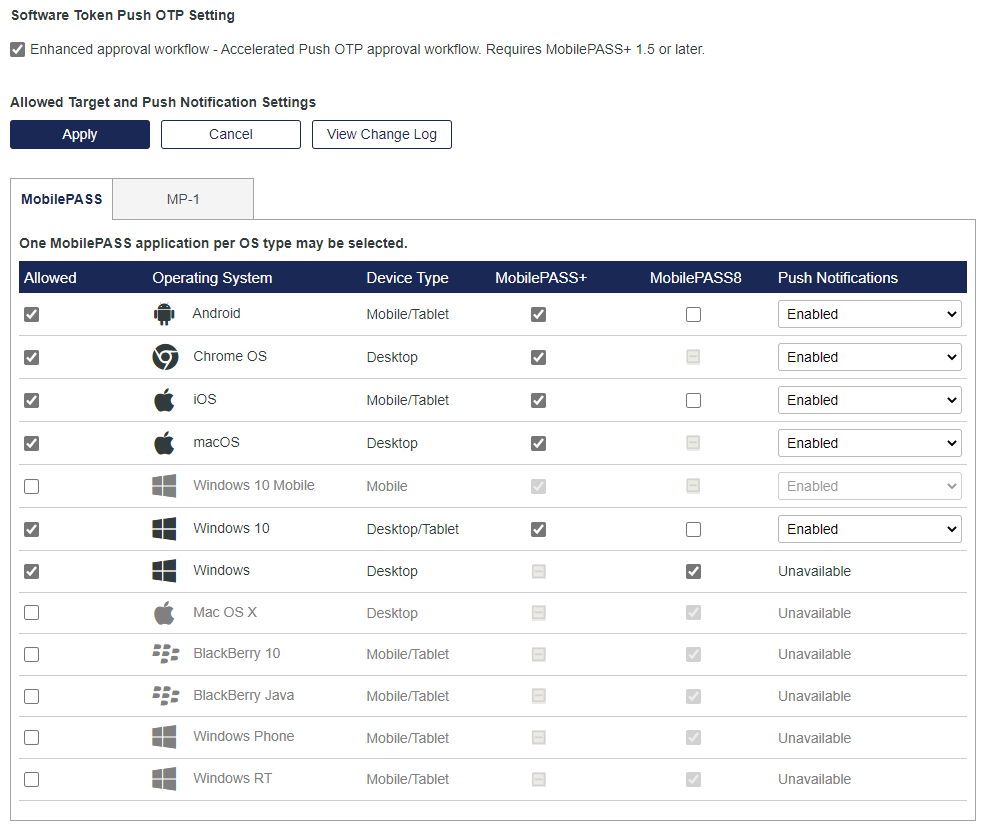
In the Allowed Target and Push Notification Settings, select the Allowed check box and the check box for each platform.
MobilePASS+ token self-provisioning is available for the following operating systems and devices:
Operating system Device type Android Mobile/tablet Chrome Desktop iOS Mobile/tablet macOS Mobile/tablet Windows 10 Desktop/tablet -
To allow Push Notifications for an allowed platform, select Enabled.
-
Select Apply.
Configure the MobilePASS+ passcode and PIN requirements
Token templates provide the operating parameters, such as passcode or PIN strength, for a token. The templates are applied every time a token is enrolled.
You can customize the token templates, and therefore token operation, to adapt to changes in your security policy. Customizing a template does not affect tokens that are already initialized and does not affect tokens that are assigned to users.
-
On the STA Token Management console, select Policies > Token Policies > Token Templates.
-
In the Type list, select MobilePASS, and then select Edit.
-
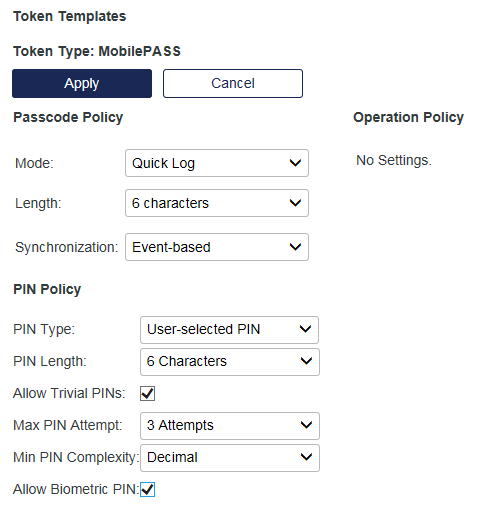
Configure the passcode and PIN settings:
Parameter Description Passcode Policy Mode Tokens can operate in either Challenge-Response or Quick Log mode. Quick Log mode is recommended because it simplifies the user login experience and strengthens security by eliminating the requirement to have the user key a challenge into a token to get an OTP.
Length The length determines the number of characters displayed as the OTP. The options are 6 characters (default) or 8 characters. Synchronization - Time-based: Determines the number of seconds the user has for authentication, before another passcode is generated.
- Event-based: Ensures that a unique passcode is generated on every button-press (for hardware tokens), or when the app is opened or the renew button is clicked.
PIN Policy PIN Type This setting determines the type of PIN to be used with the token:
- No PIN: The user does not need to use a PIN. The token generated password is sufficient for authentication.
- User-selected PIN: The user must enter the correct PIN into the MobilePASS+ app before an OTP is generated. To log in to a service, the user enters only the OTP at the password prompt. For example, if the user PIN is 8432 and the password is 12345678, the user enters 12345678 at the password prompt.
The user must change the PIN that is generated for the token during initialization before an OTP is generated. Thereafter, the user can change the PIN at any time. The new PIN must conform to the minimum requirements for PIN length and complexity.
- Server-side User Select: To log in to a service, the user must append or prepend the PIN to the OTP that is generated in the MobilePASS+ app, which allows the PIN to be evaluated by the virtual server. For example, if the user PIN is ABCD, and it must be prepended to the password 12345678, the user enters ABCD12345678 at the password prompt.
The user can change the PIN that is generated for the token. The new PIN must conform to the minimum requirements that are set in the server-side PIN policy.
PIN Length Determines the PIN length that can be used with the MobilePASS+ token.
- If the PIN Type is set to No PIN, this option is disabled. The user will not be required to use a PIN at any time.
- If the PIN Type is set to Server-side User Select, this option is disabled. The user must use a PIN according to the options set in Policy > Token Policies > Service-side PIN Policy.
- If PIN Type is set to User selected PIN, this option is enabled. This requires that any PIN set for the token meets the indicated minimum number of digits. The range is 4 to 8 characters.
Allow Trivial PINs If enabled, a PIN can be three or more consecutive numbers (for example, 1234), or three or more identical digits (for example, 2222). Default value: Not selected.
Max. PIN Attempt This option is available only if the PIN Type is set to User selected PIN. It determines the maximum number of consecutive failed PIN attempts permitted by the token. If this number is exceeded, the token is locked and cannot be used for authentication until it is reinitialized. Min PIN Complexity - If PIN Complexity is set to Decimal and Allow Trivial PINs is selected, the user can use a PIN with any consecutive or repeated characters, such as 1111, 1234, 6543, abcd, or aaaa.
- If PIN Complexity is set to Decimal and Allow Trivial PINs is disabled, the user can use either a Numeric or an alphanumeric PIN, as long as it does not consist of consecutive or repeated characters. For example, aaaa or 1234 are not permitted, while 9946, 123682, 321aaa, or i6gfaa are permitted.
- If PIN Complexity is set to Strong alphanumeric, the user must use an alphanumeric PIN that includes at least one uppercase and one lowercase character, and one number, such as 1Qazxs8 or ajUys36.
Allow Biometric PIN If enabled, users can use a fingerprint sensor or facial recognition instead of typing a PIN to access their MobilePASS+ token. This option requires that the PIN Type is set to User-selected PIN.
The biometric PIN (Touch ID or Face ID for iOS devices, or Windows Hello for Windows devices) policy setting on STA is applied to tokens at the time of enrollment only. After a token is enrolled, policy changes on $STA do not affect the availability of the biometric PIN feature on that token. Default value: Disabled.
- Select Apply.
View an audit trail for self-provisioning
On the STA Token Management console, the Enrollment History Report includes all enrollments, including self-provisioned tokens.
On the STA Access Management console, the audit logs list the configuration changes and the self-provisioning attempts.
How users self-provision a MobilePASS+ token
Self-provisioning is triggered when an access policy requires an OTP and the user does not yet have a token. It forces the user to enroll a token before they can log in. After the user enrolls the token, they can use it immediately, to continue logging in.
The instructions for installing the authenticator and enrolling a token are provided in the language that is specified in the browser settings. Users can select a different language. If the instructions are not available in that language, the English instructions are displayed.
For a description of the self-provisioning procedure, see:

