Flexible Passwordless Authentication Journeys
In cases where a user has a valid authenticator, but cannot use it, Flexible Passwordless Authentication Journeys enables them to use an alternate.
This feature is available for the global policy, exception policies, and scenarios, but not for the logon policy.
Options
-
Configure up to:
- three primary authenticators
- three secondary authenticators
Authenticators between primary and secondary sets must be distinct and cannot be a subset of one another.
-
If Identity Providers (IDP) are included in both sets:
-
If the other primary and secondary authenticators are identical, the IDPs must be different.
For example:
- Primary authenticators = OTP + IDP(A)
- Secondary authenticators = OTP + IDP(B)
The authenticators required by each IDP can be the same.
-
If the other primary and secondary authenticators are different, the IDPs can be identical.
For example:
- Primary authenticators = Password + IDP(A)
- Secondary authenticators = OTP + IDP(A)
For more information, see IDP orchestration.
-
Operation
When configuring a policy, if the first authenticator is the same in both sets, and the primary set is selected first, then the primary's first authenticator will default to the secondary's first authenticator and vice versa. In addition, the secondary's first authenticator will be disabled. Any changes made in the requirements of the primary's first authenticator will be applied to the secondary's first authenticator. This case is an exception to IDPs.
Configuration
To configure Flexible Passwordless Authentication Journeys:
-
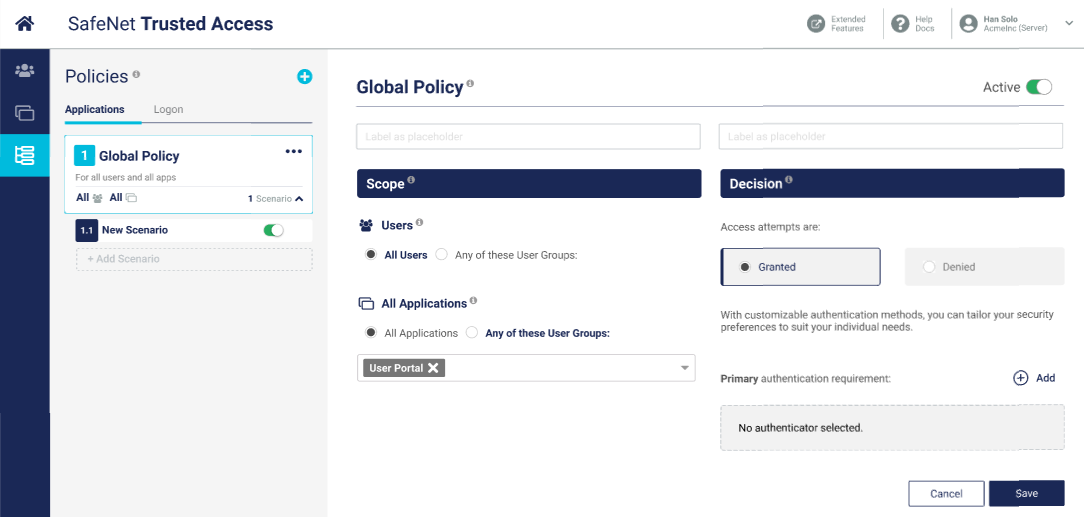
On the STA Access Management console, select Policies and then select the Applications tab.
-
Select the desired policy, for example Global Policy.
-
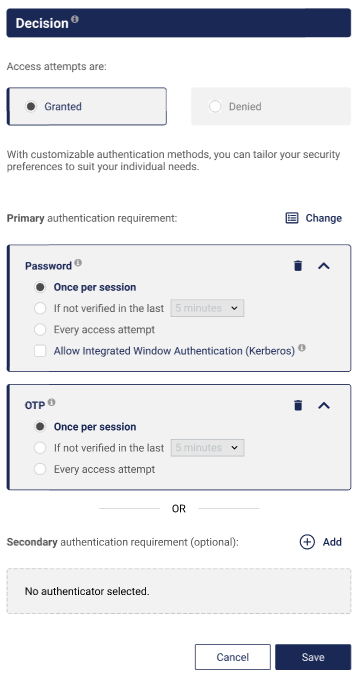
Select Edit and then select Add in the Primary authentication requirement section under Decision.
-
Select the primary authenticators, for example, Password and OTP. See Authentication for a list of authenticators supported by STA.
-
Select OK.
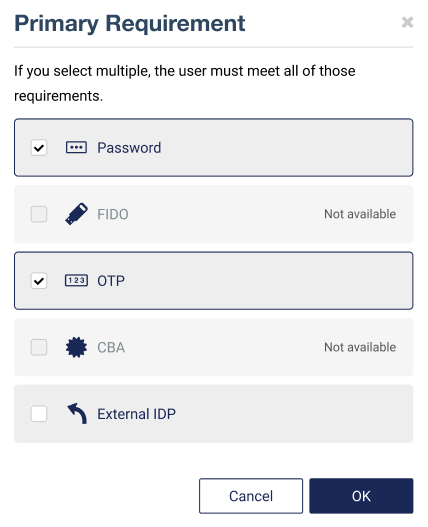
As you select authenticators, some of the remaining options may become unavailable. This indicates which authenticators are mutually exclusive.
-
To add an alternate authenticator, select Add under Secondary authentication requirement.
-
Select the secondary authenticators, for example FIDO and then select OK.
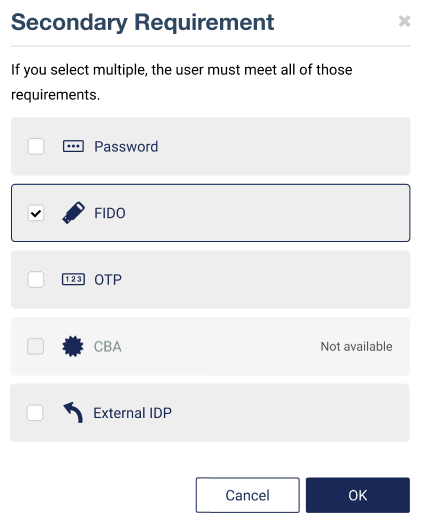
To use Integrated Windows Authentication (Kerberos), Password must either be selected or deselected in both the primary and secondary authentication methods.
-
Select Save to save your changes.
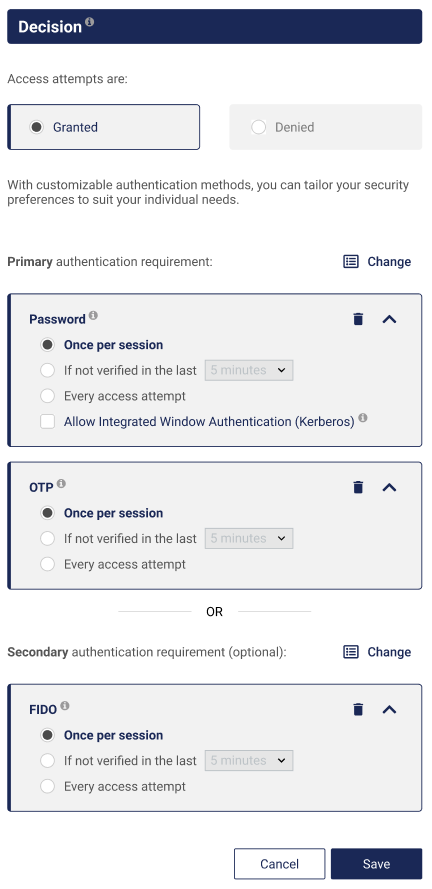
You cannot save a policy if the uniqueness requirements between the primaary and secondary authentication methods is not observed. If Save is disabled, change the selections and retry.
The user experience
In this example, an account is configured with the following authentication requirements:
- Primary: Password
- Secondary: OTP or FIDO
An example user-workflow follows:
-
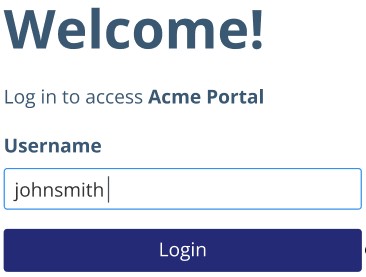
The user attempts to open a protected resource, such as the User Portal.
-
The user enters their username.
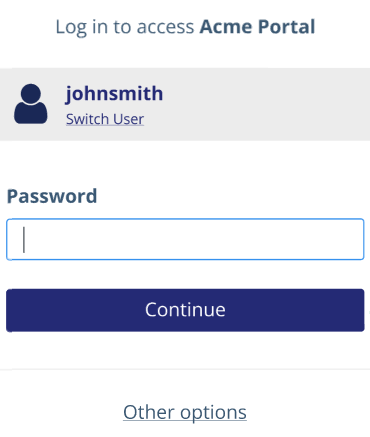
The user's primary authentication method displays. If a password is required, the system will request it first. If an external IDP is required, the system will request it last.
-
The user selects Other options to choose a secondary authenticator if, for example, they forgot their password. The link displays only when additional options are configured.
-
The user selects Passkey so that they can use their FIDO passkey, instead of their password, to login.
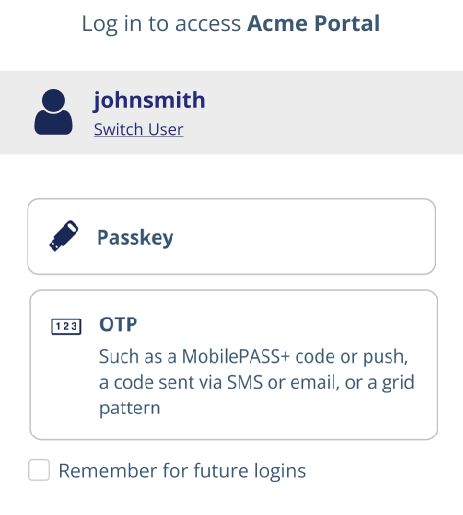
When the first authenticator is the same in both primary and secondary requirements, then the second authenticators configured for the primary and secondary requirements are displayed.
If the selected primary or secondary authenticator is External IDP, the system will not display the Remember for future logins option.
-
The user follows the browser instructions for their FIDO passkey.
After successful authentication, the protected resource opens.

