SafeNet MobilePASS+ authenticators
SafeNet MobilePASS+ authenticators requires the STA or STA Premium plan.
The STA Access Management console lists all of the SafeNet MobilePASS+ authenticators deployed to your users and identifies the level of risk associated with the host devices.
Acquisition of risk data requires SafeNet MobilePASS+ 2.0 or later.
View SafeNet MobilePASS+ authenticators
To view a list of SafeNet MobilePASS+ authenticators:
-
In the STA Access Management console, select the Home tab.
-
Select the MobilePASS+ Authenticators tab.
All SafeNet MobilePASS+ 2.0 authenticators display in descending order from the time of last use.
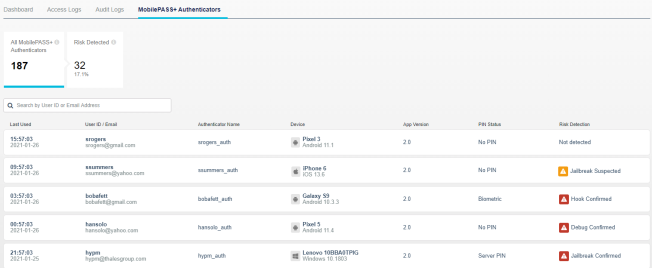
-
In the summary at the top, select Risk Detected to display the at-risk authenticators only.
SafeNet MobilePASS+ authenticator details
The list of SafeNet MobilePASS+ authenticators includes the following information:
| Column | Description |
|---|---|
| Last Used | The time of the last access attempt made with the SafeNet MobilePASS+ authenticator. |
| UserID / Email | The user ID and email address of the user who made the access attempt. |
| Authenticator Name | The name of the SafeNet MobilePASS+ authenticator that was used for the access attempt. This name is configured by the user in the token settings of the SafeNet MobilePASS+ app. |
| Device | Name and model information, based on the device's operating system:
|
| App Version | The version of the SafeNet MobilePASS+ application used by the authenticator. |
| PIN Status | Type of PIN required to authenticate:
|
| Risk Detection | The risk associated with the SafeNet MobilePASS+ authenticator. See Risk detection states. |
Risk detection states
The risk detection states for each operating system include the following information:
| Risk State | Description | Android | iOS | Windows |
|---|---|---|---|---|
| Debug | SafeNet MobilePASS+ is running in a debugging environment, exposing all security-relevant data, compromising the token. | safe, suspected, or confirmed | - | safe or confirmed |
| Hook | A function hook or hooking framework was detected which allows skimming of security critical secrets, like token shared secrets or PIN’s. | safe, suspected, or confirmed | safe, suspected, or confirmed | safe, suspected, or confirmed |
| Jailbreak | The mobile device is jailbroken, which allows all OS built-in security mechanisms to be bypassed. Security of the token secrets cannot be guaranteed. | - | safe, suspected, or confirmed | - |
| Root | The mobile device is rooted, which allows all OS built-in security mechanisms to be bypassed. Security of the token secrets cannot be guaranteed. | safe, suspected, or confirmed | - | - |
Risk detection state values
-
Safe - no risk detected
-
Suspected - some signals indicated a risk, but the data is inconclusive. Could be a false positive
-
Confirmed - risk is confirmed
Risk detection updates
Android
On Android devices, the application will send the risk data randomly within eight hours of activating the first authenticator. Any updates to the risk detection data will be sent on subsequent application launches or push notification responses, delayed by approximately 30 seconds.
iOS and Windows
On iOS and Windows devices, during the 48 hours following enrollment of the first token, a random check at each application launch determines whether the data will be sent; with a probability of 20%. After 48 hours, risk detection data is sent on each application launch for which a change has been detected.
Data update triggers
Risk detection updates are triggered by:
-
SafeNet MobilePASS+ application upgrade
-
Device operating system upgrade
-
Token information update (new token enrollment, token deletion, token alias change)
-
User PIN change
-
Biometric setting change (enable/disable)
-
Device push setting change (enable/disable push from the device setting)
-
Risk state change (device is hooked, rooted/jailbreak, debugger attached)

