TLS support is added to the Luna Network HSM 7 syslog implementation, to encrypt log messages being sent to a remote server. This improves security of your logs by preventing their interception during transit. Such protection is desirable to safeguard details that could reveal the current state of the appliance.
NOTE This feature requires minimum Luna Appliance Software 7.8.3.
Revised existing commands, and new commands, under syslog remotehost support
>Server authentication with self-signed certificates.
>Server authentication with CA-signed certificates.
>Mutual authentication with self-signed certificates.
>Mutual authentication with CA-signed certificates.
This feature is implemented in Luna Network HSM 7 appliance software, and does not require update of the HSM firmware, nor of the Luna HSM Client.
Caveats
The use of NTP is advised, to keep the Luna Network HSM 7 and remote syslog servers in sync.
In the initial implementation, all CA-signed server and client certificates must be signed by the same entity. That is a consideration if you are configuring multiple remote syslog servers.
NOTE The Luna Network HSM 7 appliance is the client in the syslog interaction, and so the CA certificate used to encrypt communication with a remote syslog server is not shown when performing "client addCA" for connections from clients looking to access the HSM.
Remotehost cannot be added for the same host and the same port, using TCP and UDP at the same time.
Multiple remote host syslog servers with CA-signed certificates can be used. For self-signed certificates, a single remote host syslog server, only is accepted.
Commands
The following commands are added under lunash:>syslog remotehost cert to support the use of TLS while connecting to remote syslog servers.
>syslog remotehost cert delete
>syslog remotehost cert deleteCA
>syslog remotehost cert install
>syslog remotehost cert installCA
>syslog remotehost cert status
The following pre-existing commands were modified to support the use of TLS while connecting to remote syslog servers.
syslog remotehost add adds -mode, -name, and -tls options
Sample workflows
Example: Configure for Server authentication with self-signed certificates.
>The remote syslog server generates a private key and self-signed certificate.
>The remote syslog server passes the root certificate to the Luna Network HSM 7 appliance.
>Luna Network HSM 7 appliance adds this certificate to its trust store.
>User configures server information.
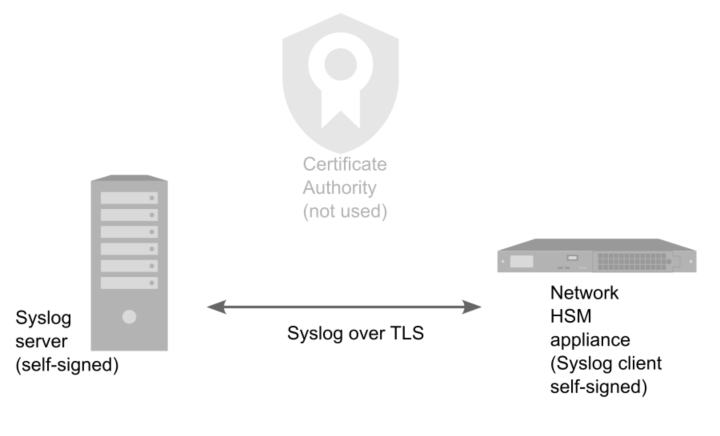
1.Generate a self-signed certificate on the syslog server.
2.Copy this certificate to the Luna Network HSM 7 appliance in the user space of the user, having admin or operator role, that will be handling system logging.
#scp -O server_self_cert.pem admin@192.168.10.93: admin@192.168.10.93's password: server_self_cert.pem 100% 1318 1.2MB/s 00:00
3.Add the remote server configuration.
lunash:>syslog remotehost add -host 192.168.140.45 -protocol relp -port 514 -mode mutual -tls -name server.rsyslog.com Stopping syslog: [ OK ] Starting syslog: [ OK ] 192.168.140.45 added successfully Make sure the rsyslog service on 192.168.10.45 is properly configured to receive the logs Command Result : 0 (Success) [lnh93] lunash:>syslog remotehost list Remote logging server(s): ========================= [192.168.140.45]:514, relp, tls Command Result : 0 (Success)
4.Execute a lunash command and ensure that the log entry from the LNH is received on the remote server.
[lnh93] lunash:>hsm show Appliance Details: ================== Software Version: 7.8.3-288 HSM Details: ============ HSM Label: Pri_LNH1 Serial #: 593658 Bootloader: 1.1.5 Firmware: 7.8.2 HSM Model: Luna K7 HSM Part Number: 808-000073-001 Authentication Method: Password : : etc... Command Result : 0 (Success) [lnh93] lunash:>
... and on the server...
2023-07-11T12:01:40.444982-04:00 192.168.141.93 [localhost] hsm[29662]: info : 0 : Command: hsm show : admin : 192.168.53.104/56001
Remote server authentication with mutual authentication and self-signed certificates.
>The Luna Network HSM 7 appliance generates a self-signed client certificate.
>The remote syslog server retrieves the self-signed certificate from the Luna Network HSM 7 appliance.
>The remote syslog server generates a private key and self-signed certificate.
>The remote syslog server passes the root certificate to the Luna Network HSM 7 appliance.
>Luna Network HSM 7 appliance adds this certificate to its trust store.
>User configures server information.
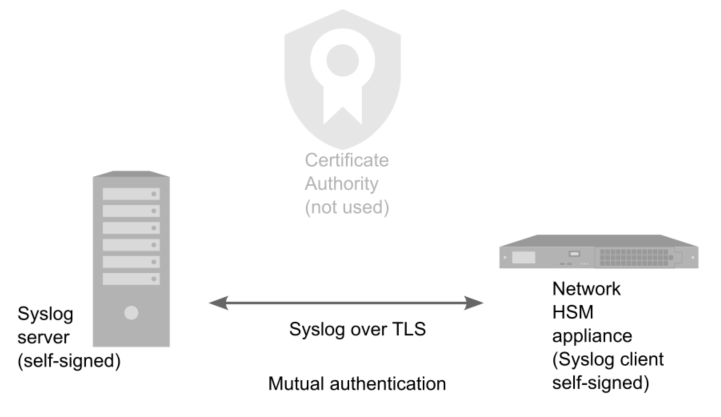
Example: Configure a remote server with mutual authentication and self-signed certificates
1.Generate a certificate.
lunash:>syslog remotehost cert gen -san DNS:foo.com Certificate generated successfully. The syslog service needs to be (re)started before a secure connection can be enabled. Command Result : 0 (Success)
2.Import this certificate to the server and add it to the server configuration. The client certificate file is in the file area reserved to the user, having the admin or operator role, that generated it, so that user's credentials are required when the remote syslog server requests the file via scp/pscp.
From a remote logging server
scp admin@192.168.141.93:client_syslog.pem <localFileLocation>
and you are prompted for the password of the named user on the Luna Network HSM 7 that created the file
(or use pscp on Windows, with the same syntax).
At the remote server add the client_syslog.pem file to the server configuration as appropriate to your remote syslog instance.
3.Import the server certificate and add it.
lunash:>syslog remotehost cert installCA server_self_cert.pem Attempting to install server_self_cert.pem CA certificate installed successfully. The syslog service needs to be (re)started before a secure connection can be established. Command Result : 0 (Success)
4.Add the remote server configuration.
lunash:>syslog remotehost add -host 192.168.10.45 -protocol relp -port 514 -mode mutual -tls -name server.rsyslog.com Stopping syslog: [ OK ] Starting syslog: [ OK ] 192.168.140.45 added successfully Make sure the rsyslog service on 192.168.10.45 is properly configured to receive the logs Command Result : 0 (Success) [lnh93] lunash:>syslog remotehost list Remote logging server(s): ========================= [192.168.140.45]:514, relp, tls Command Result : 0 (Success)
5.Execute a lunash command and ensure that the log entry from the LNH is received on the remote server.
[lnh93] lunash:>hsm show Appliance Details: ================== Software Version: 7.8.3-288 HSM Details: ============ HSM Label: Pri_LNH1 Serial #: 593658 Bootloader: 1.1.5 Firmware: 7.8.2 HSM Model: Luna K7 HSM Part Number: 808-000073-001 Authentication Method: Password : : etc... Command Result : 0 (Success) [lnh93] lunash:>
... and on the server...
2023-07-11T12:01:40.444982-04:00 192.168.141.93 [localhost] hsm[29662]: info : 0 : Command: hsm show : admin : 192.168.53.104/56001
Mutual authentication with CA signed certificates
>The remote syslog server and the Luna Network HSM 7 appliance each generate a private key and CSR.
>The remote syslog server and the Luna Network HSM 7 appliance add the received signed certificates.
>The remote syslog server and Luna Network HSM 7 appliance add the CA certificate to their trust store.
>User configures server information.
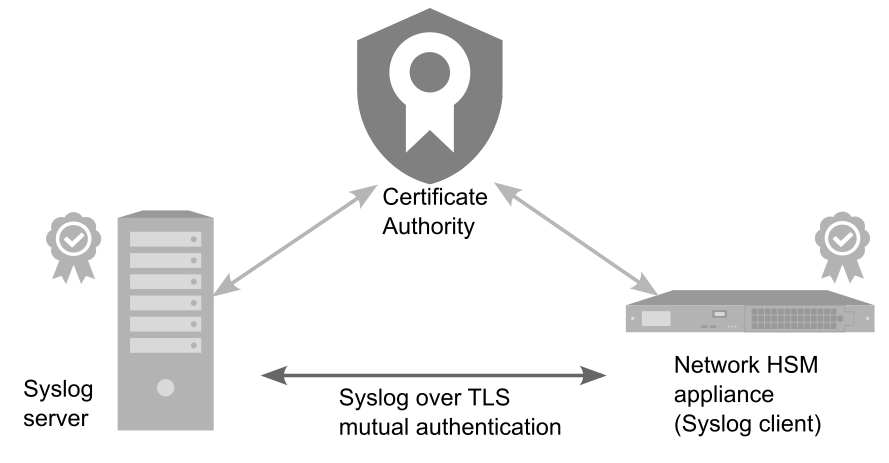
Example: Configure a remote server with mutual authentication, tcp and CA-signed certificates
1.Generate a CSR.
lunash:>syslog remotehost cert gen -csr
2.Export the CSR and sign it with the CA certificate.
3.At the CA server receive the CSR, sign the cert from the Luna Network HSM 7 appliance and return it.
[CAserver]# scp operator@192.168.14.93:client_syslog_csr.csr . [CAserver]# <CAserver-side command(s) to sign the cert> [CAserver]# scp ca.pem operator@192.168.14.93: [CAserver]# scp client_sign.pem operator@192.168.14.93:
4.Add the CA certificate to the Luna Network HSM 7 appliance.
lunash:>syslog remotehost cert installCA ca.pem Attempting to install ca.pem CA certificate installed successfully. The syslog service needs to be (re)started before a secure connection can be established. Command Result : 0 (Success)
5.Import the signed client certificate to the Luna Network HSM 7 appliance and add it.
lunash:>syslog remotehost cert install client_sign.pem Attempting to install client_sign.pem HSM certificate installed successfully. The syslog service needs to be (re)started before a secure connection can be enabled. Command Result : 0 (Success)
6.Add the remote server configuration.
lunash:>syslog remotehost add -host 192.168.140.45 -protocol tcp -port 514 -mode mutual -tls Stopping syslog: [ OK ] Starting syslog: [ OK ] 192.168.140.45 added successfully Make sure the rsyslog service on 192.168.140.45 is properly configured to receive the logs Command Result : 0 (Success)
7.Execute a command in lunash and ensure that the log entry from the Luna Network HSM 7 appliance is received on the server.
lunash:>syslog remotehost list Remote logging server(s): ========================= [192.168.140.45]:514, tcp, tls Command Result : 0 (Success)
...at the server...
Jun 21 14:25:37 192.168.141.93 [localhost] hsm[13889]: info : 0 : Command: syslog remotehost list : admin : 192.168.106.144/62166
Mutual authentication multiple servers, with CA signed certificates.
>The remote syslog servers each generate a private key and CSR and get the CSR signed from the CA.
>The Luna Network HSM 7 appliance generates a private key and CSR and gets the CSR signed from the CA.
>The remote syslog servers add the acquired certificate.
>Luna Network HSM 7 appliance adds the CA certificate to its trust store.
>User configures server information.
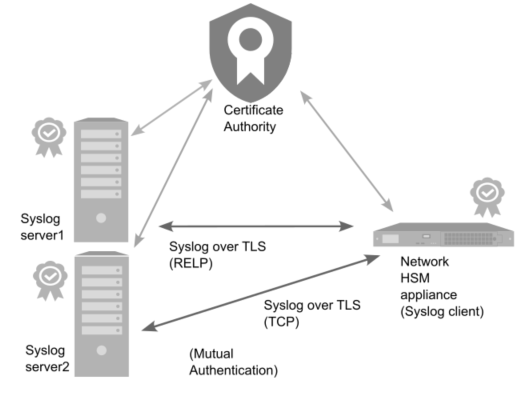
Example: Configure multiple remotehost syslog servers with mutual authentication and CA-signed certificates (all servers active)
Prerequisite
Two remote syslog servers are used in this example.
To configure a Luna Network HSM 7 appliance with two remote syslog servers
1.At the Luna Network HSM 7 (IP address 192.168.14.93 in this example), which is to be the client to the remote syslog server(s), generate a certificate and certificate signing request.
lunash:>syslog remotehost cert gen -csr
2.At the CA server receive the CSR, sign the cert from the Luna Network HSM 7 appliance and return it.
[CAserver]# scp operator@192.168.14.93:client_syslog_csr.csr . [CAserver]# <CAserver-side command(s) to sign the cert> [CAserver]# scp ca.pem operator@192.168.14.93: [CAserver]# scp client_sign.pem operator@192.168.14.93:
3.Add the CA certificate to the Luna Network HSM 7 appliance.
lunash:>syslog remotehost cert installCA ca.pem
4.Import the signed client certificate to the Luna Network HSM 7 appliance and add it.
lunash:>syslog remotehost cert install client_sign.pem
5.At the first remote syslog server, configure to receive logs from the Luna Network HSM 7
6.At the Luna Network HSM 7 appliance add the CA certificate, from the first remote syslog server, to the appliance's trust store.
lunash:>syslog remotehost add -host 192.168.143.48 -protocol relp -port 514 -tls -name server.rsyslog.com -mode mutual lunash:>syslog remotehost list Remote logging server(s): ========================= [192.168.13.48]:514, relp, tls
7.At the second remote syslog server, configure to receive logs from the Luna Network HSM 7
8.At the Luna Network HSM 7 appliance add the CA certificate, from the second remote syslog server, to the appliance's trust store.
lunash:>syslog remotehost add -host 192.168.143.45 -protocol tcp -port 514 -tls -name server.rsyslog.com -mode mutual
9.At the Luna Network HSM 7 appliance run commands that can be logged to the remote syslog servers.
lunash:>syslog remotehost list Remote logging server(s): ========================= [192.168.14.45]:514, tcp, tls [192.168.13.48]:514, relp, tls Command Result : 0 (Success) lunash:>hsm show
10.Verify that both remote syslog servers are working with this client Luna Network HSM 7 by checking for log entries for the commands that were just run.
Server1
2023-06-28T10:44:34.538875-04:00 192.168.141.93 [localhost] hsm[31002]: info : 0 : Command: syslog remotehost list : operator : 192.168.106.144/56917 2023-06-28T10:45:29.734290-04:00 192.168.141.93 [localhost] hsm[31002]: info : 0 : Command: hsm show : operator : 192.168.106.144/56917
Server2
2023-06-28T10:44:34-04:00 192.168.141.93 [localhost] hsm[31002]: info : 0 : Command: syslog remotehost list : operator : 192.168.106.144/56917 2023-06-28T10:45:29-04:00 192.168.141.93 [localhost] hsm[31002]: info : 0 : Command: hsm show : operator : 192.168.106.144/56917
