Networking
Luna Network HSM 7s support multiple different network configurations via:
Network Interfaces
The Luna Network HSM 7 appliance enables flexible network configurations by way of multiple network interfaces that can be configured in various ways.
Ethernet Ports
The Luna Network HSM 7 appliance has four 1Gb/a Ethernet LAN ports and one RJ-45 serial port, used for initial network configuration.
The network device interfaces (eth0, eth1, eth2, and eth3) and serial port are located on the rear of the appliance, as illustrated in HSM Appliance Ports:
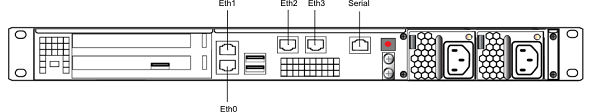
Each Ethernet (Eth) port can be used to configure an individual network device, or the interfaces can be combined to enable a redundant network configuration. (See Network Interface Bonding.)
You use the serial port to connect a serial device to the Luna Network HSM 7 for access to LunaSH to perform initial network configuration. You will need to use the serial port to configure at least one of the network interfaces. Once you have configured an interface, you can connect the appliance to the network and access LunaSH to complete the network configuration.
Network Interface Bonding
Luna Network HSM 7 has four physical network interface devices: eth0, eth1, eth2, and eth3. You can bond eth0 and eth1 into a single virtual interface, bond0, or eth2 and eth3 into bond1, to provide a redundant active/standby interface.
Network Interface Bonding shows how individual devices (marked by eth) can be combined to create a bonded device.
Figure 2: Network Interface Bonding

Network traffic can be bound to a single device, or a bonded device. The primary purpose of the bonding service is a hot standby mode for network interface failure, ensuring a constant stable connection to your appliance.
Once bonding is configured, client connections as well as SSH connections continue uninterrupted if either or the bonded interfaces fails.
NTLS and STC
Luna Network HSM 7 supports network connections over two different types of channels:
>NTL (Network Trust Link)
>STC (Secure Trusted Channel)
Network Trust Link Server
Network Trust Links (NTLs) are secure, authenticated network connections between the Luna Network HSM 7 appliance and clients. NTLs use two-way digital certificate authentication and TLS data encryption to protect your sensitive data during all communications between HSM partitions on the appliance and its clients.
NTLS Connection shows how an NTLS connection is made between the client and the appliance.

Certificates are created on both the appliance and the client. These certificates are exchanged to register the appliance and client with each other. Once registered, the appliance will recognize the client and allow it access to the HSM and partitions it wants. NTLS encrypts data between the network interfaces of the appliance (shown as eth0 in the diagram) and client, but not between the network interface and the cryptographic module within the appliance; if you require end-to-end encryption that terminates inside the cryptographic module, see the next section for Secure Trusted Channel.
Secure Trusted Channel
Secure Trusted Channel (STC) uses secure key exchange and data encryption to protect your sensitive data during communications between HSM partitions and clients. The type of data encryption you use is up to you; STC is flexible and customizable.
STC supports a wide range of end-points, but its primary end-points are client applications connecting to the HSM to access its cryptographic services and/or to perform module management functions. STC provides three basic services:
>Privacy of all communicated data through the use of symmetric encryption so only the end-points can read any sensitive data.
>Integrity of the communicated data through the use of message authentication codes so that not eavesdropper could add, delete, modify or replay any command or response.
>Mutual authentication of the HSM and the end-point so that only authorized entities can establish a STC connection and there can be no man-in-the-middle attack.
STC Connection shows how an STC connection is made between the client and the appliance.

STC connects a client directly to a specific partition on the HSM in the appliance.
The STC connection consists of two phases: tunnel establishment and message handling. During tunnel establishment the end-parties perform bi-directional authentication and then establish unique session keys for each connection. After a connection is established between the network interfaces of the appliance (shown as eth0 in the diagram) and client, the message handling phase securely transmits commands to the HSM and receives HSM responses. Any attempt to alter, insert or drop messages is detected by both end-points and results in immediate termination of the connection.
NTLS must be set up before you use STC.
Comparing NTLS and STC
| NTLS | STC |
|---|---|
|
>Consistent high performance >Not recommended for use with public networks |
>Exceptionally secure and safe to use with public networks >Customizable parameters >Performance depends on parameters set |
For detailed instructions on setting up NTLS or STC, see Client-Partition Connections.
