Management
Agent Side
Use SafeNet Windows Logon Agent Manager to configure various options available within the agent.
Note
- To use all features of the Windows Logon Agent Manager, you must work in Run as Administrator mode.
- The SafeNet Windows Logon Agent Manager cannot be accessed by a domain administrator from a trusted domain using administrator rights.
The following tabs are available to configure various settings. These tabs are available only to users who are part of the Local Administrators and Domain Administrators groups. All other group members will only see the Off-line tab.
Off-line
The Off-line tab deals with the following end-user offline authentication settings.
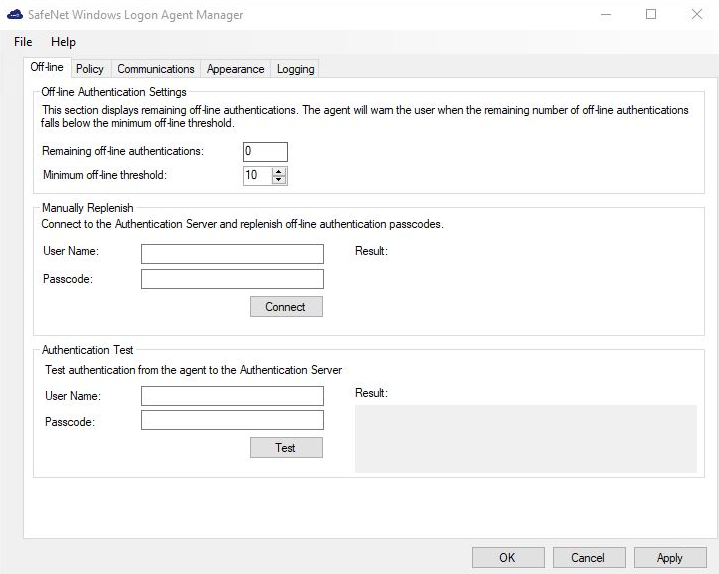
Off-line Authentication Settings
The agent allow users to log in to their workstations when STA is not available.
-
Remaining off-line authentications: The total number of available offline authentications for all the authenticators.
To modify the default value of offline authentications, navigate to Policy > Token Policies > Token Passcode Processing Policy of STA.
Default: Configured value in STA
Range: 2-500
-
Minimum off-line threshold: The user will see a warning to authenticate against STA or perform a manual replenish if this value is reached.
Default: 10
Range: 5-99
Manually Replenish
The offline store is automatically replenished when a user returns and logs in to the corporate network. If the offline store expires while the user is still at a remote location, the Manually Replenish option allows admin user to refill their offline authentication store.
To replenish an offline authentication store manually, perform the following steps:
-
Establish a VPN connection to the corporate network.
-
Open the SafeNet Windows Logon Agent Manager as an administrator.
-
Enter user's SafeNet credentials into the Passcode field and click Connect.
-
The agent contacts STA to verify the logon credentials. If the credentials are valid, the offline authentication is restored; otherwise, the user will receive a warning message to retry the authentication attempt.
Authentication Test
This allow administrators to test authentication between the agent and STA.
Policy
The Policy tab allows SafeNet authentication exclusions to be applied to the agent.
After changing the settings on the Policy tab, the updated settings are enforced either after the machine restart or after a successful online authentication with STA, for each user.
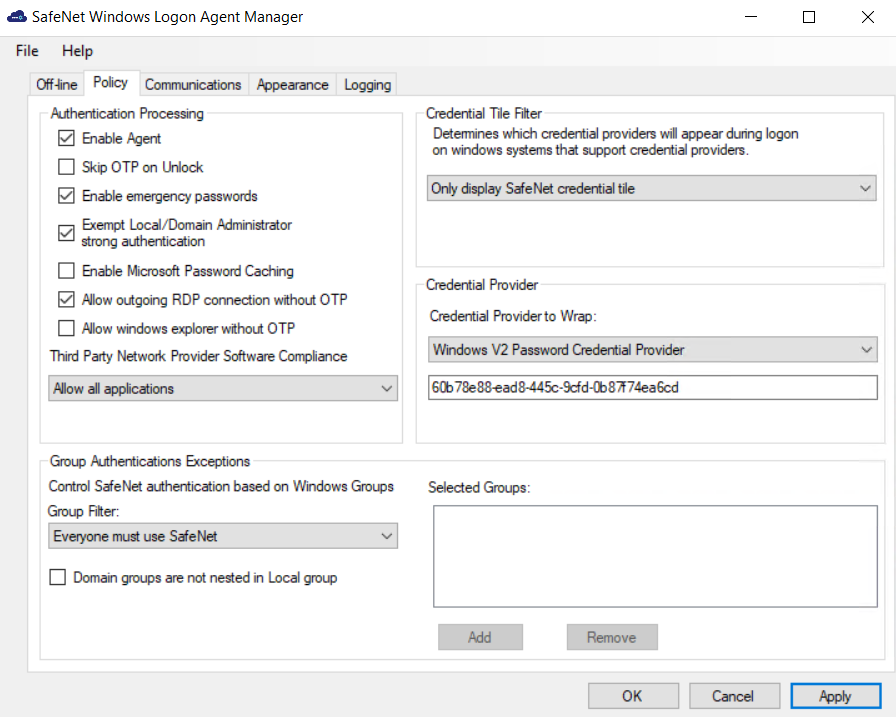
Authentication Processing
Authentication Processing section specifies the options to be enabled or disabled while processing the authentication.
-
Enable Agent: Used to enable or disable the agent.
Default Setting: Enabled
-
Skip OTP on Unlock: Allows the administrators to enable or disable the SafeNet 2FA for last logged on user on system unlock.
The value for Skip OTP on Unlock is synced with the value configured in the STA console, hence it is advisable not to alter the checkbox in the management console.
The functionality extends to sleep and hibernate modes, which means that if the Skip OTP on Unlock checkbox is selected, and the system enters sleep or hibernate mode, the agent does not prompt for an OTP, and instead logs in successfully using only the AD credentials.
Default Setting: Disabled
This setting is not yet supported in Remote Desktop Access.
-
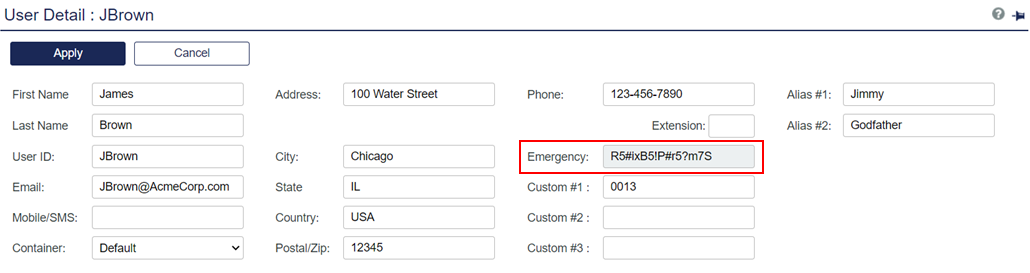
Enable emergency passwords: Allows a user to authenticate using an emergency password in offline mode, typically when off-line authentications are exhausted (Remaining off-line authentications = 0).
This is applicable only in the case of offline mode.
Default Setting: Enabled
Each user has a unique emergency password, which is set on the Secured Users tab of STA. This password can be used until the workstation regains contact with STA.
-
Exempt Local/Domain Administrator strong authentication: Allows the Local and Domain Administrator groups to be exempt from SafeNet authentication during login.
Default value: Determined during agent installation
This feature does not work with pure Azure AD joined machines for domain admins. However, this feature works as expected for the local admins.
-
Enable Microsoft Password Caching: Used to enable or disable the Microsoft Password Caching mode.
Microsoft Password Caching mode: For accessing a WLA protected machine, each user authenticates with OTP first, followed by the Microsoft password. In this mode, the user is prompted for their Microsoft password only once for their first log in. Subsequently, the agent caches the Microsoft password until its expiry or change.
This feature does not work for the following:
- Domain admin users
- Users authenticating via the Use a grid pattern link. To use this feature for GrIDsure token, enter "g" character in the Password field. -
Allow outgoing RDP connection without OTP: Enables STA authentication to be bypassed when making an outgoing RDP connection.
This feature is not effective if the Microsoft parameter,
enablecredsspsupport:i:0, is set to null, which controls credentials usage on the Operating System level for RDP. -
Allow windows explorer without OTP: Allows Windows explorer to run without SafeNet Authentication (bypass STA OTP option). It is invoked when a network path is accessed or an application is run with other user credentials.
While accessing a network resource on a domain different than domain of the WLA protected machine, OTP is not prompted. The Windows password must be provided in the Passcode field to access the resource.
-
Third Party Network Provider Software Compliance: Select one of the following options:
-
Allow all applications (Default): Allows to install the agent without updating the registry keys under [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\NetworkProvider\Order].
Sometimes, selecting this option creates a conflict between the agent and the third-party network provider software. In this case, you need to uninstall the third-party network provider software and remove its registry entry. Before executing this operation, you need to perform the following steps:
1. Ensure that the Allow all applications option is selected.
2. Click Apply and close the management console. -
Allow only SafeNet compliant applications: Allows to reset the registry key under [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\NetworkProvider\Order] to “ProviderOrder"=" RDPNP,LanmanWorkstation,webclient ". After selecting this option, all the registry keys will be removed, except the following:
-
"ProviderOrder"="RDPNP,LanmanWorkstation,webclient "
-
SafeNet compliant keys, such as “PICAClientNetwork”
-
If you change the option from Allow only SafeNet compliant applications to Allow all applications and apply the changes, the registry state under [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\NetworkProvider\Order] will be restored to the previous state.
This option is to increase the security via the agent, where it restricts certain third-party network providers from allowing the user to bypass the SafeNet authentication. However, some third-party credential provider software may conflict with the working of the SafeNet Agent for Windows Logon. So, you can restrict their access with this registry key and only allow certain supported software to work with the agent.
-
Credential Tile Filter
The Credential Tile Filter determines which credential providers are allowed to display the credential tiles on the login screen.
-
Only display SafeNet credential tile: SafeNet credential tile is displayed on the login screen with the authentication flow (OTP + Microsoft password). All other (third-party) credential tiles are hidden.
-
Hide Microsoft credential tile: SafeNet credential and third-party credential tiles are displayed on the login screen. The Microsoft credential tile is hidden.
-
Hide SafeNet credential tile and show all available: Third-party and Microsoft credential tiles are displayed on the login screen. The SafeNet credential tile is hidden.
An 'Incompatible Filter' warning may be displayed if a conflicting credential provider filter entry is listed at the following path:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Provider Filters
In such a case, the warning will be displayed with two user-response options:
-
Yes: removes the conflicting registry entry.
-
No: disable the agent.
Credential Provider
The Credential Provider determines the version of a credential provider to be created and dynamically wrapped.
-
Credential Provider to Wrap: Allows the agent to dynamically wrap Microsoft or other external third-party Credential Providers’ GUID.
-
This option defaults to Windows V2 Password Credential Provider. The subsequent text field will auto-populate the relevant GUID.
-
To wrap another external (third-party) credential provider, select Other Credential Provider, and enter its GUID in the subsequent text field.
-
A popularly used external credential provider ServiceNow Password Reset tool is already configured to wrap. However, it will only be visible if ServiceNow is installed and running on the system.
Before uninstalling a third-party credential provider, it is advisable to unwrap it first.
Group Authentication Exceptions
The Group Authentication Exceptions section allows to omit single or multiple local or domain groups from performing SafeNet authentication. Only one group filter option is valid at any given time, and it cannot overlap with another group authentication exception.
Default setting: Everyone must use SafeNet
MFA will not work (as configured) if Primary group is added in the Group Authentication Exception.
-
Group Filter: Select one of the following drop-down option:
- Everyone must use SafeNet: All users must perform SafeNet authentication.
- Only selected groups will bypass SafeNet: All users are required to perform SafeNet authentication, except for the defined Microsoft group(s).
- Only selected groups must use SafeNet: Users are not required to perform SafeNet authentication, except for the defined Microsoft group(s).
This feature does not work with pure Azure AD joined machines for domain groups. However, this feature works as expected for the local groups.
-
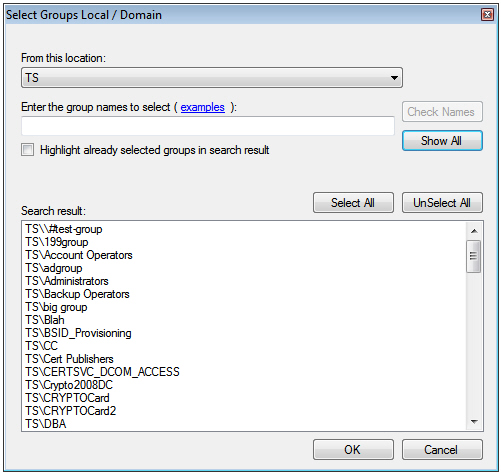
Selected Groups: Click Add. The Select Groups Local / Domain window will be displayed:
- From this location: Displays local or domain search results. The search results will not be visible in case of pure Azure AD joined machines.
- Enter the group names to select: Used in conjunction with Check Names or Show All, and allows searches for Microsoft groups.
- Highlight already selected groups in search result: If a Microsoft group has already been configured in the exception, it will appear as a highlighted result.
-
Domain groups are not nested in Local group: If selected, indicates that no Nested Groups (Domain groups are nested in the Local group) are present in the Selected Groups field. Domain lookup is skipped in such a case, helping improve the login delay time.
Communications
This tab deals with the connection options for STA.
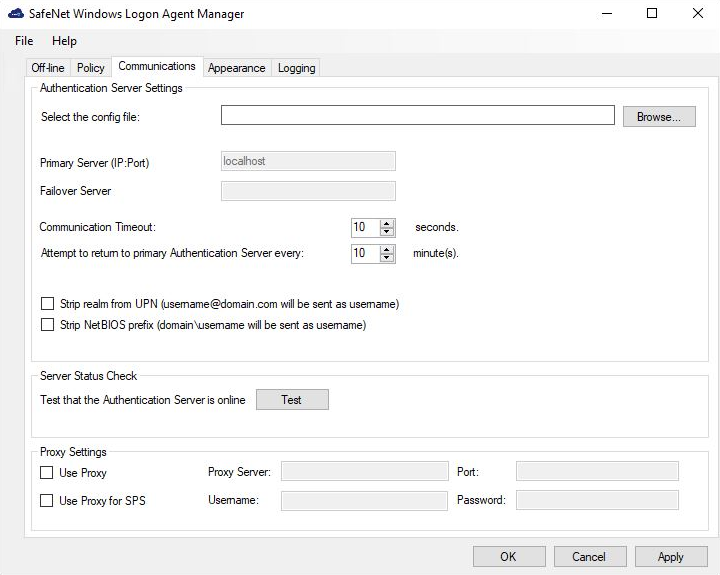
Authentication Server Settings
-
Agent Config file: Used when the agent configuration file is browsed. Next to the Select the config file field, click Browse to specify the location of the agent’s configuration file.
To update the Agent.bsidkey file, download the Agent.bsidkey file from STA, and perform the following steps:
-
Log in to your SafeNet Trusted Access account, and navigate to COMMS > Authentication Processing.
-
Under Task list, click Authentication Agent Settings link and download the Agent.bsidkey file.
-
Update the downloaded file at the <Agent installation location>\Keyfile location.
If the WLA application is open on the STA page, a new BSIDKEY is created for the tenant. To download the new BSIDKEY, refresh the STA page.
To configure the updated agent file, refer to Configuring the updated agent file section in Installing the agent section.
-
-
Primary Server: This is the STA Primary server URL.
-
Failover Server: This is the STA Failover server URL.
-
Communication Timeout: Specifies the maximum timeout value for authentication requests sent to STA.
Minimum value: 1 second. Do not set a value below the minimum prescribed limit in the registry.
Default value: 10 seconds. It is highly recommended to use the default value.
-
Attempt to return to primary Authentication Server every: Specifies the primary authentication server retry interval. This setting only takes effect when the agent is using the Failover Server.
-
Strip realm from UPN (username@domain.com will be sent as username): Select if the STA username is required without the suffix @domain.
-
Strip NetBIOS prefix (domain\username will be sent as username): Select if the STA username is required without the prefix domain\.
Note
- The realm-stripping feature applies to STA usernames only. AD usernames are not affected.
- If a Username Format is selected earlier in the Share tab in STA, then you do not need to select the checkbox in the management console.
Server Status Check
Under this section, click Test to run a communication test to verify a connection to STA.
Proxy Settings
-
Use Proxy: Select to connect to STA via proxy server.
-
Use Proxy for SPS: Select to connect to the Service Provider Server via proxy server.
-
Proxy Server: Enter IP address of the proxy server.
-
Port: Enter proxy server port.
Ensure that the port is open in Windows network.
-
Username: Enter proxy server user name.
-
Password: Enter proxy server password.
Select the proxy settings, as follows:
Configuration |
Without Proxy | With Proxy (all calls) | With Proxy and TVP (non-push calls go to TVP, push calls go to proxy) |
With Proxy for STA (or TVP behind Proxy) and Proxy for SPS |
| Proxy Settings | ||||
| Use Proxy | Not selected | Selected | Not selected | Selected |
| Use Proxy for SPS | Not selected | Not selected | Selected | Selected |
The (Proxy) Password should always be set using the SafeNet Windows Logon Agent Manager, ensuring that it is stored encrypted. The key ProxyPassword should never be set instead using the Registry/ADMX file.
Appearance
This tab allows to customize the logo displayed during authentication.
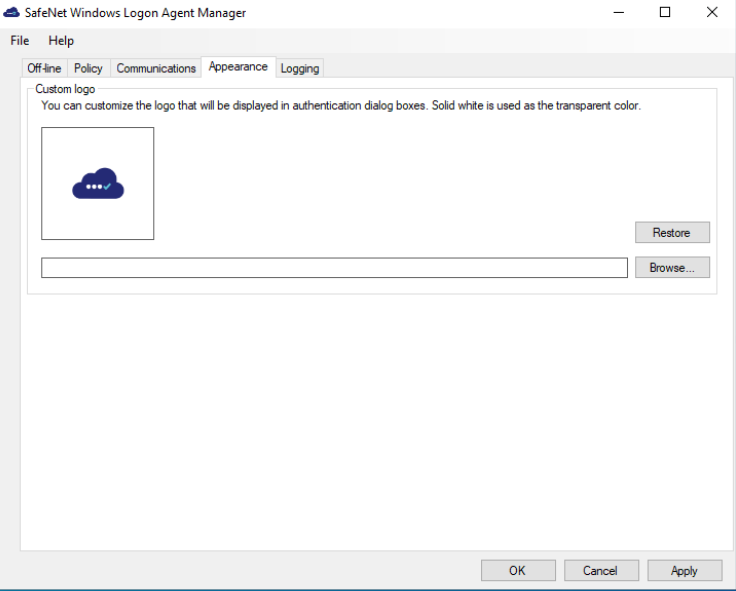
Custom logo
This configuration is used to customize the logo in authentication dialog box.
The logo file must be saved on the local computer. We recommend saving it in the SafeNet Agent for Windows Logon installation folder or any other protected location.
-
The custom logo must be a bitmap of 110 x 110 pixels. Solid white will be used as the transparent color if the image is smaller than 110 x 110 pixels.
-
The Restore option will revert to the default STA logo.
Logging
This tab depicts the logging level and specifies the log file location.
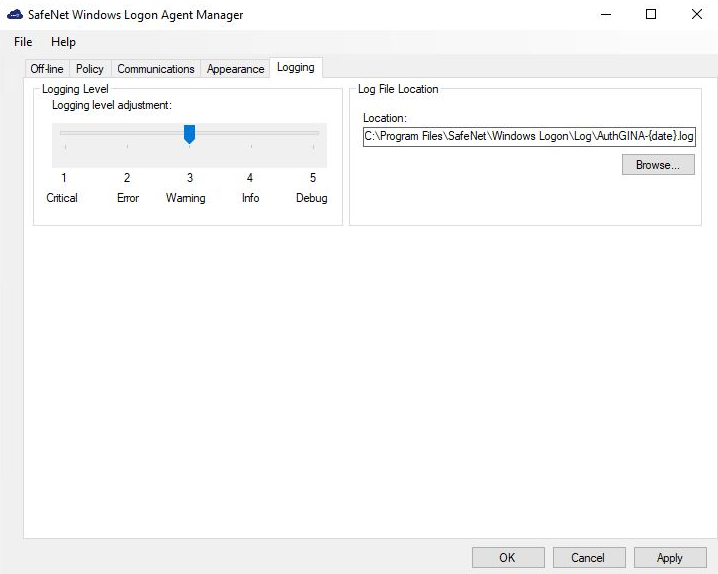
Logging Level
This setting adjusts the logging level. Drag the pointer on the Logging level adjustment scale to the required level:
-
1 – Critical: Very severe error events that might cause the application to terminate.
-
2 – Error: Error events that prevent normal program execution, but might still allow the application to continue running.
-
3 – Warning: Potentially harmful error events. (Default)
-
4 – Info: Informational error events that highlight the progress of the application.
-
5 – Debug: Detailed tracing error events that are useful to debug an application. (Recommended)
Log File Location
It specifies the location where the log files are saved. The log files are rotated on a daily basis.
Default location: C:\Program Files\SafeNet\Windows Logon\Log\AuthGINA-{date}.log
To address logs vulnerability, one additional log directory will be created in the default location with name LogonUI specifically for privileged process LogonUI.
Additional location for LogonUI process: Default location\LogonUI\LogonUI--{date}.log
STA Side
Logon Policies
The logon policy applies to every logon agent that is configured on the Applications tab in STA. The logon policy does not apply to versions of the agent that are not configured on the Applications tab. The logon policy has no effect until a logon agent is configured on the Applications tab and then deployed.
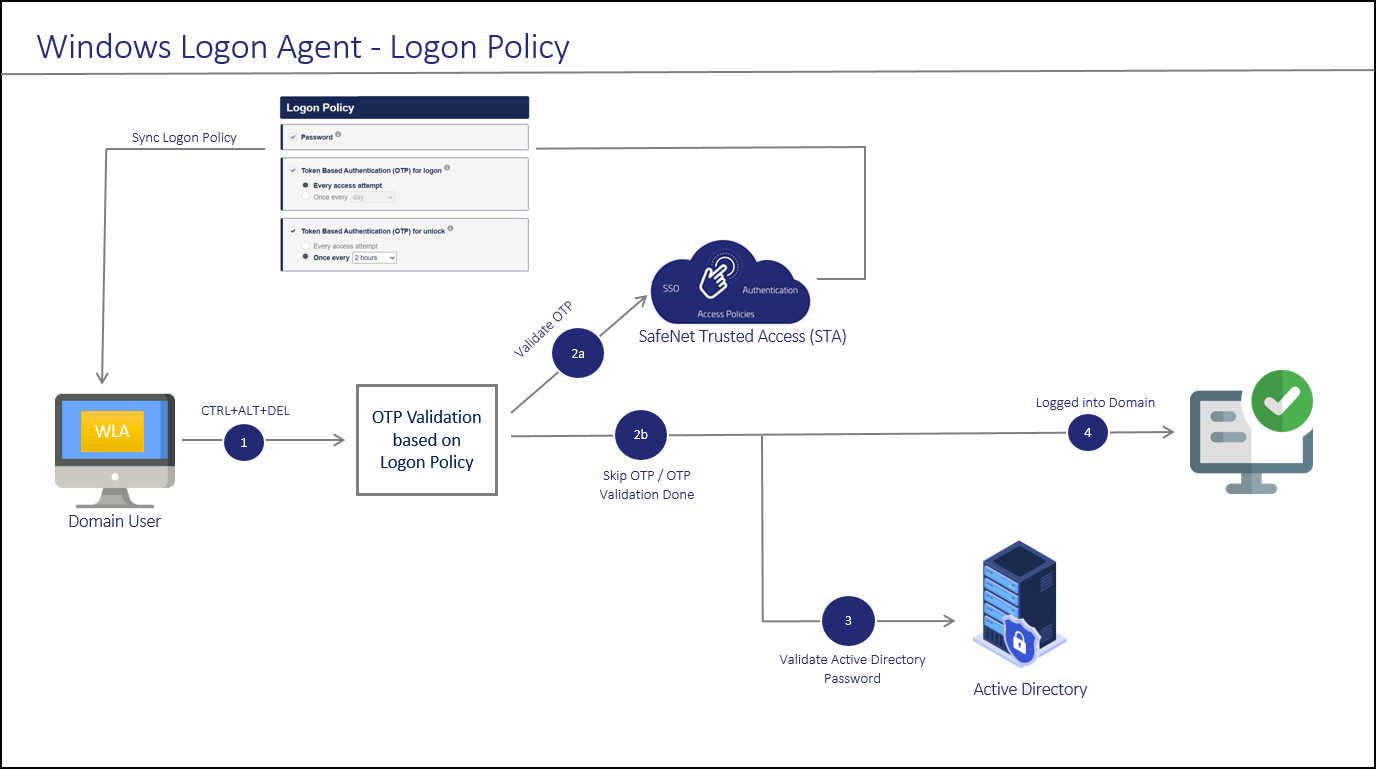
The logon policy is evaluated only when the user's machine is running the logon agent. It allows you to specify whether the user must provide their one-time password (OTP) on the lock screen.
-
After invoking the workstation logon, the user is presented with a STA Windows Logon prompt.
-
If Multi-Factor Authentication is required, the user enters the credential of the supported second factor authentication, for example, OTP. The entered credentials are then sent to the STA for verification on the basis of logon policy. After the successful OTP validation, the logon policies are synced with the agent. Otherwise, if the user is part of a domain group authentication exception, the credentials are passed to Active Directory (AD).
-
If the STA credentials are valid, the user is prompted for Microsoft password. If Microsoft Password Caching mode is enabled, the user is prompted for the Microsoft password only the first time they log on. Subsequently, the agent will cache the Microsoft Windows password, furnishing it as required.
-
On successful validation of the Microsoft credentials, the user is logged on to the WLA installed machine.
Configure the Global Logon Policy
By default, the global logon policy applies to all users and to every SafeNet Agent for Windows Logon that is configured on the Applications tab. This means that the logon policy applies to every machine that is running the agent.
You can configure whether the user must provide their OTP for re-authentication.
-
On the STA management console, select the Policies tab.
-
Select the Logon tab.
-
If this is your first time accessing the Logon policies tab, select Set Your Global Logon Policy. After you save the global logon policy, this prompt no longer displays.
-
If the Set Your Global Logon Policy prompt does not display, on the Global Logon Policy for STA, select Edit.
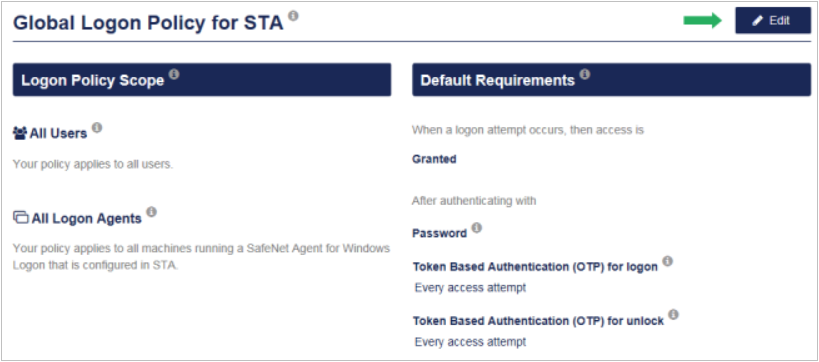
By default, the global logon policy for STA applies to all users and all logon agents. When a logon or unlock attempt occurs, then access is granted after authenticating with the domain password and OTP. Only the options under Token Based Authentication (OTP) are configurable.
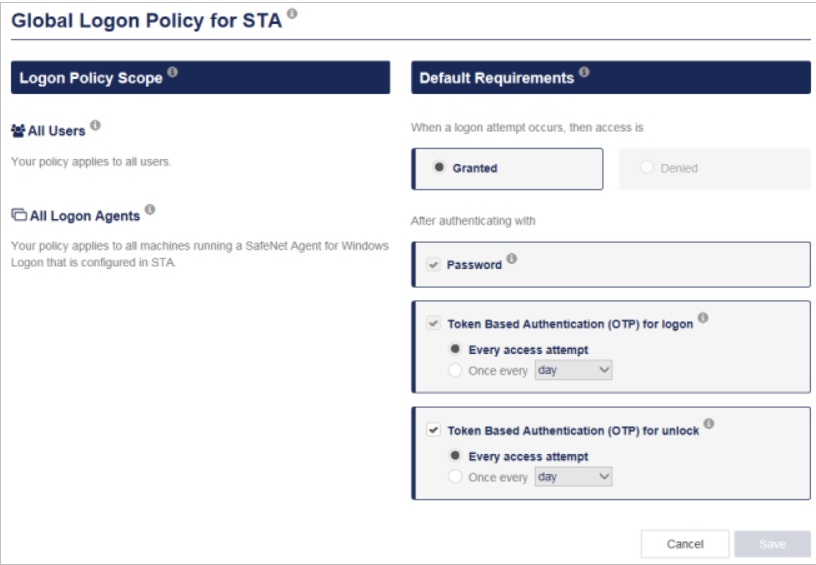
-
Under Token-Based Authentication (OTP) for logon, select the re-authentication requirement:
-
Every access attempt: Users are prompted for their OTP every time they log on.
-
Once every <period>: Users are prompted for their OTP only once each <period> when they log on.
- STA supports periods of: 1, 2, 3, or 8 hours; 1, 2, or 3 days; or 1 week.
-
-
Under Token-Based Authentication (OTP) for unlock, select the re-authentication requirement:
-
Every access attempt: Users are prompted for their OTP every time they unlock their machine.
-
Once every <period>: Users are prompted for their OTP only once each <period> when they unlock their machine.
- STA supports periods of: 1, 2, 3, or 8 hours; 1, 2, or 3 days; or 1 week.
-
-
Select Save.
-
On the Congratulations screen, select I'm Done.
The logon policy has no effect until SafeNet Agent for Windows Logon is configured on the Applications tab and then deployed.
-
To configure SafeNet Agent for Windows Logon, select the Applications tab and add an agent.
Specify the IP addresses to synchronize with the policy or configure the SafeNet Agent for Windows Logon.
Specify IP addresses
The SafeNet Agent for Windows Logon enables you to base the unlock policy on the location of the user by using network conditions to define the IP addresses that are valid for the user. The network condition checks whether the access attempt originates inside or outside the IP address ranges that you specify.
The re-authentication time for Windows unlock is determined based on the public IP range that is specified in the policy. After the re-authentication time expires, users who are enabled with this policy are prompted for an OTP.
-
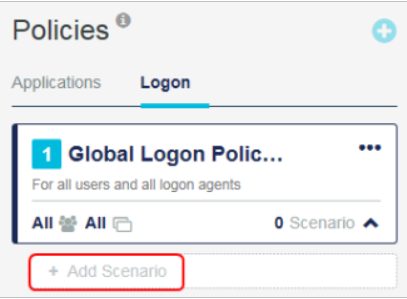
Below the Global Logon Policy for STA, select Add Scenario.
-
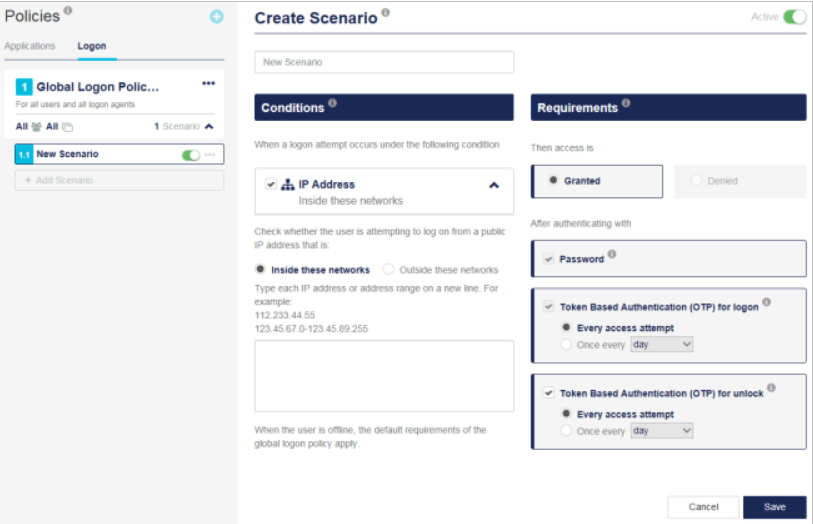
In the Conditions section, ensure that the IP Address condition is selected and expanded.
-
Select one of the following options:
-
Inside these networks: Checks whether the access request originates from an IP address that is included in the network.
-
Outside these networks: Checks whether the access request originates from an IP address that is not included in the network.
-
-
In the text box, enter each IP address or IP address range on a new line, and use these formats:
-
Single IP address: 1.1.1.1
-
Range of IP addresses: 1.1.1.1-1.1.1.255
-
-
Select Save.

