Set up Hardware Security Module in Normal mode
Prerequisite: This procedure assumes that the SAS server is already installed, and running on the system. If the SAS server is not installed, install it by following the instructions provided at the following link: https://thalesdocs.com/gphsm/ptk/protectserver3/docs/integration_docs/index.html.
During setup, different applications and utilities must be able to access the HSM slots directly. The HSMs are initially configured to operate in the Normal mode. After the initial setup is complete, the utilities that need access to the system in High Availability (HA) mode must be configured.
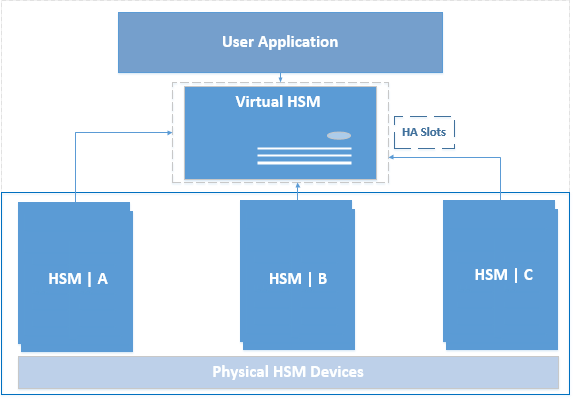
The HA mode is required for mission-critical applications that require uninterrupted uptime. It allows multiple HSM devices to be grouped together to form a virtual device, ensuring that the service is maintained even if one or more physical devices is unavailable.
The HA slots are required since they act as virtual slots between the physical HSM(s) and the user application. An HA slot shares the same token label as the HSM slot (associated with it), and thus communicates with the user application on behalf of the HSM. The following figure illustrates the schema.
Install and configure Protect Toolkit C package
To install and configure the Protect Toolkit C (PTKC) package, complete the following steps: The steps need to be completed on the SAS server, and all other sites for that SAS instance.
Optional Step: To allow the ability to readdress PSEs in the future, add HSM entries in the hosts file on your machine by following the instructions:
-
Navigate to the following path:
C:\Windows\System32\drivers\etc -
Locate the
hostsfile, open it using a Notepad, and add the HSM entries.
Configuration guidelines with PSEV2 device:
-
Install Network HSM Access Provider (
PTKnethsm.msi) package version 5.2.0. To install, follow the steps:-
Visit Service Portal (https://supportportal.thalesgroup.com).
-
Login using your User ID and Password.
If you are not registered, register as a New User at the portal, using your Customer Identifier Number (CIN).
-
Search Document ID DOW4210 in the Knowledge Base, and download.
-
Install the required package (
PTKnethsm.msipackage version 5.2.0) only.The Access Provider package enables connection to one or multiple HSMs. It acts as a data abstraction layer for which you can add multiple front-end Application Program Interfaces (APIs). To install, use the
PTKnethsm.msifile, with default settings, and continue clicking next until the Protect Server Setup popup window is displayed.Provide the HSM IP or Fully Qualified Domain Name (FQDN), and click OK.
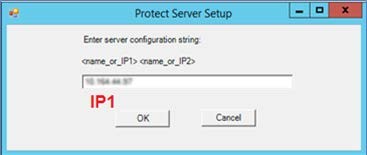
Ensure that the IP address here must belong to the HSM device 0.
The HSM device 0 is the first HSM machine that the Administrator is configuring.
If the installer is executed from a Network Share, the Protect Server Toolkit 5.2 Win64 packages do not install on 2012 R2. Copy the installer files to the local drive first, and then install. For Network HSM Access Provider package to run, the .NET Framework 3.5 is required. If you do not have the framework, download it from the following link:
https://www.microsoft.com/en-in/download/details.aspx?id=21
-
-
Install PTKC (
PTKcpsdk.msi) package version 5.2.0. To install, follow the steps:-
Visit Service Portal (https://supportportal.thalesgroup.com).
-
Login using your User ID and Password.
If you are not registered, register as a New User at the portal, using your Customer Identifier Number (CIN).
-
Search Document ID DOW4210 in the Knowledge Base, and download.
-
Install the required package (
PTKcpsdk.msipackage version 5.2.0) only.
The toolkit provides the pkcs#11 interface and talks to the access provider, which in turn routes the request to the HSM. The SAS server uses the pkcs#11 interface.
Follow the steps for installation:
-
Run
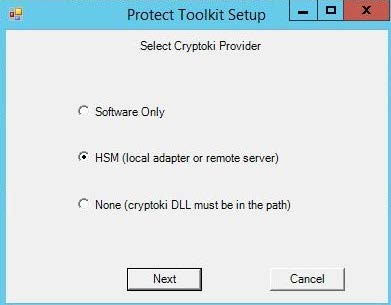
PTKcpsdk.msifile, with default settings, and continue clicking next until Select Cryptoki Provider popup window is displayed. -
Select the HSM radio button, and click Next.
-
Continue clicking next, till the installation process completes.
-
-
Check if device 0 is responding or not, by executing
HSMstate.exefile, available at the following path:C:\Program Files\SafeNet\Protect Toolkit 5\Network HSM\bin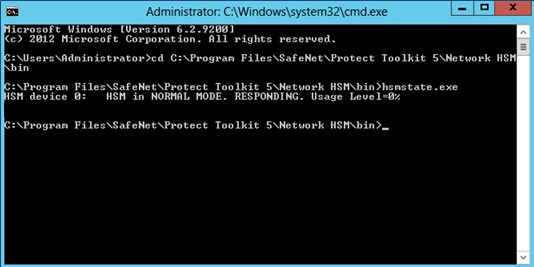
-
Restart the server to reflect changes.
Before the HSM can be configured in the SAS solution, Slot Creation and Initialization must be completed.If you require creating a key manually, or edit its attributes, refer Manual Key Generation section.
Configuration guidelines with PSEV3 device:
Install the PTKC Client 7.0.0, since the PSEv3 version is supportable with the said client version. To install, perform the steps:
-
Double click on the PTKinstaller.exe installer.
-
Under Select Components ensure that ProtectTookitSDK is selected/checked. Also, please ensure Network checkbox is selected under HSM Communication Interface like below and click Next.
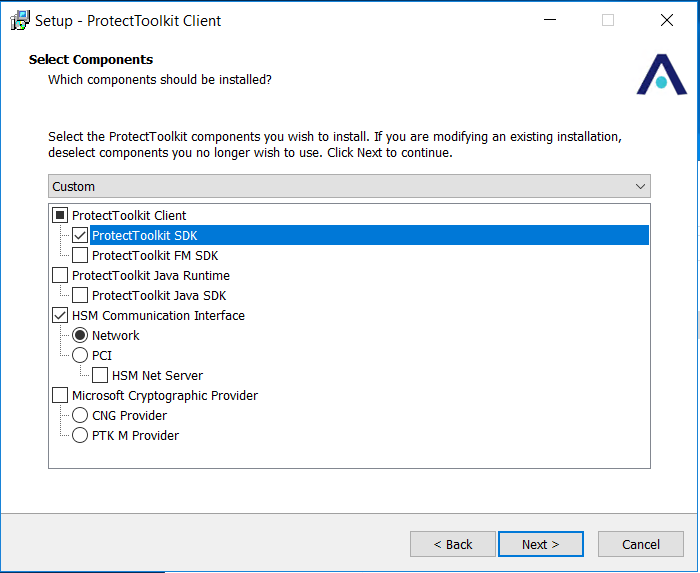
-
Under Network Configuration, provide HSM PSEv3 device IP or Fully Qualified Domain Name (FQDN) and click Next.
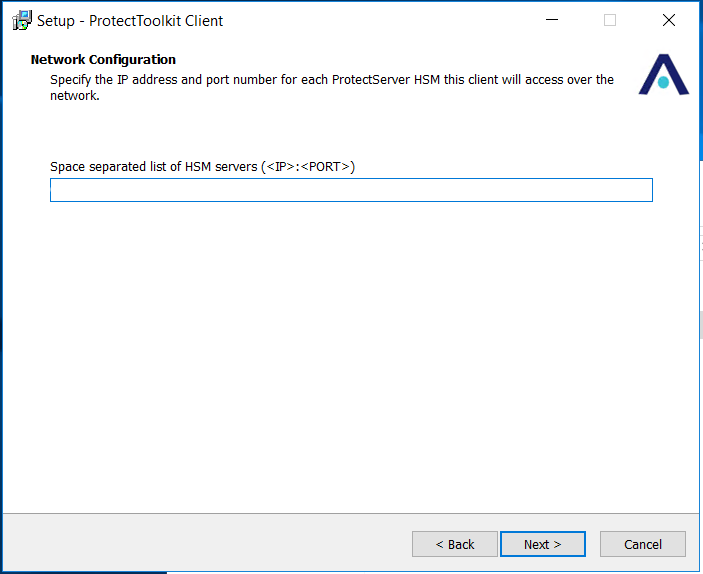
Port number is specified as 12396 by default.
-
On the SDK Configuration window, select the ProtectServer HSM option and click next.
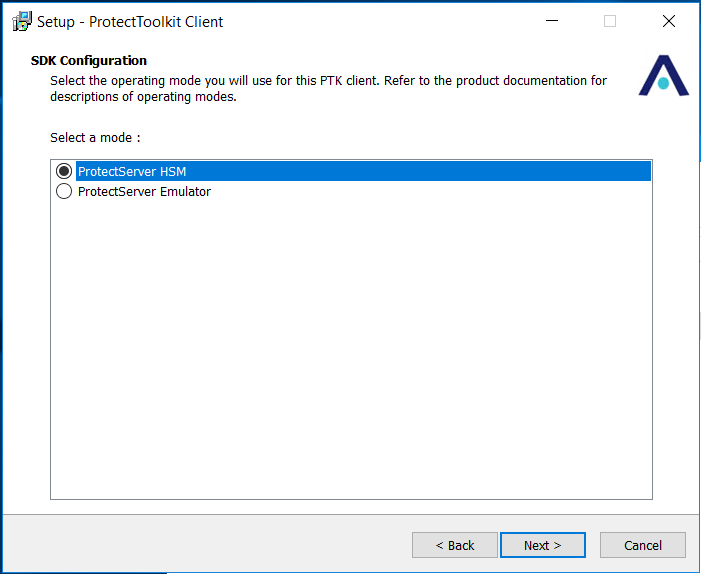
-
Finally, review settings as given below:
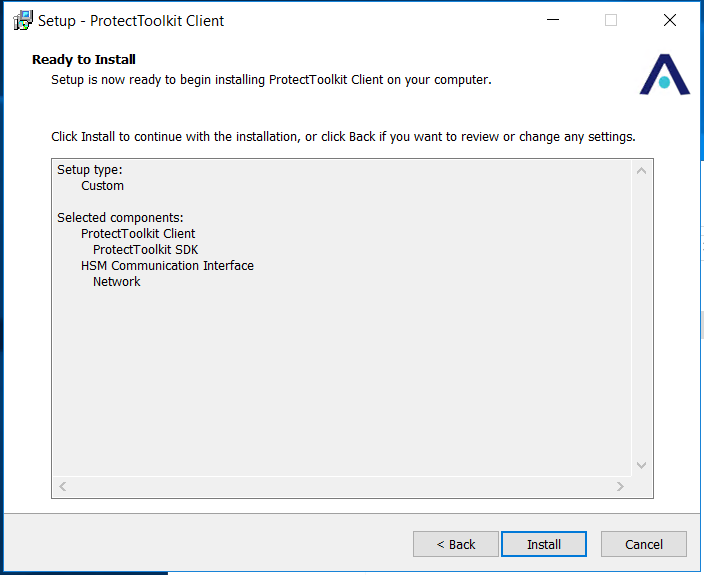
Create and initialize Slot
Install the Java Runtime Environment (https://www.java.com/en/download/manual.jsp; x64). If you do not install the Java environment, the following two batch files will not execute:
-
gCTAdmin HSM.bat -
KMU HSM.bat
In such a case, the Administrator is required to use the Command Line Interface (CLI) to configure the HSM.
Navigate to the following path:
C:\Program Files\SafeNet\Protect Toolkit 5\Protect Toolkit C SDK\bin
Follow the steps based on whether you are using the Graphical User Interface (GUI) or Command-Line Interface (CLI).
The HA setup works only if the keys are replicated on Slot 0 of device 0 HSM.
Graphical User Interface Method
-
To open, double-click the
gCTAdmin HSM.batbatch file. -
In Select an Adapter dialog box, select AdminToken option, and click OK.
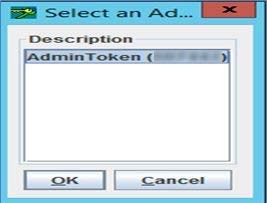
If you are unable to select an Adapter, set environment variables.
-
Enter PIN in the Enter PIN popup window, and click OK.
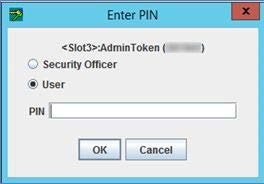
This is the same PIN as generated while setting up PSE 2 device
-
For slot creation, navigate to File > Create Slots.
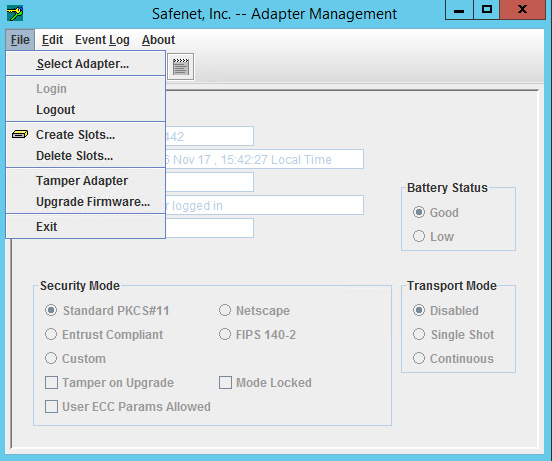
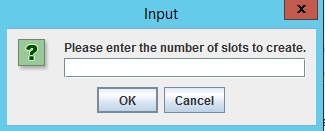
-
Enter the number of slots to be created in the Input popup window, and click OK. The tokens are created with uninitialized slots.
Example: If an Administrator enters 1 in the field, and click OK, one token is created with an uninitialized slot.
-
The Adapter Management window restarts. The Administrator needs to enter the Admin PIN.
-
To view the uninitialized slot, navigate to Edit > Tokens.
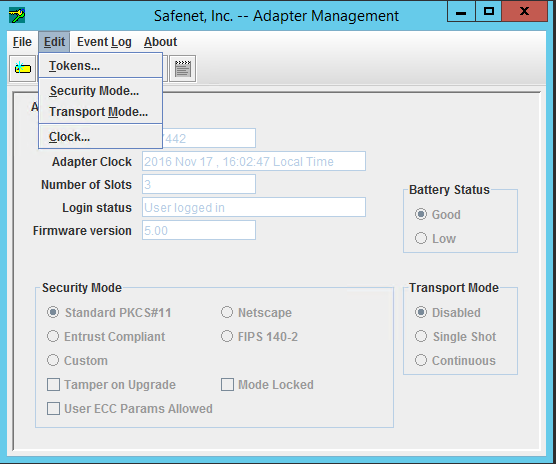
-
Select the uninitialized slot in the Manage Tokens popup window, using Slot dropdown menu, and click Initialize to initialize a slot.
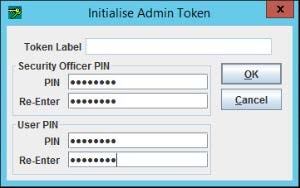
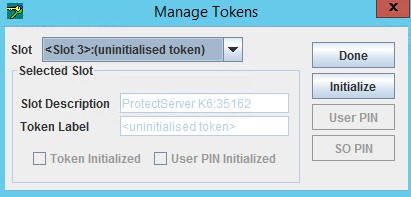
-
In Initialize Admin Token window, provide the Security Officer PIN and User PIN, and click OK.
If an Administrator wants to change PIN for a slot and is using the HA mode, the Administrator should manually change the User PIN for that slot in both HSMs or change the User PIN for one HSM and replicate the slot into another HSM using Command-Line Interface.
Command-Line Interface Method
-
To create an uninitialized slot, execute the following command:
Ctconf –a<0,1,2> –c1
Where; the first connected HSM device is numbered 0, the second as 1, and so on. Example: If there are two HSM devices to be configured, the following command sequence should be followed:
Ctconf –a0 –c1
Ctconf –a1 –c1 -
Execute the following command to configure the slot or re-initialize it, if it is already configured:
ctkmu t –s<slot number>
Example:ctkmu t –s
Configure Hardware Security Module in SafeNet Authentication Service
For fresh SAS installs (installed and enabled), the HSM encryption is applied. For existing SAS setups, the untouched data is not encrypted till a modification call is made. Once the data is modified, the HSM encryption is applied to it. Existing data may never be encrypted if it doesn’t change.
To start encrypting the data, perform the following steps:
-
Login to the SAS console as an Administrator.
-
Click the SYSTEM tab and select Setup.
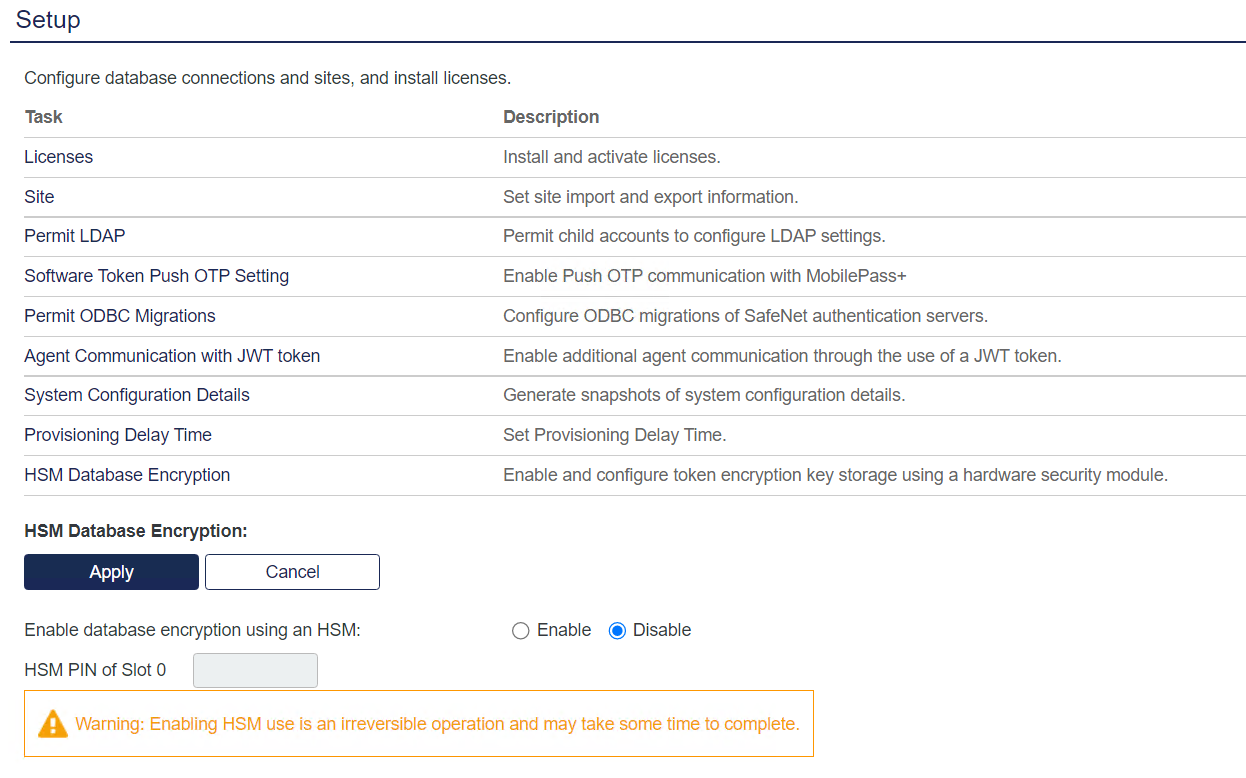
In the Setup module, click HSM Database Encryption link.
-
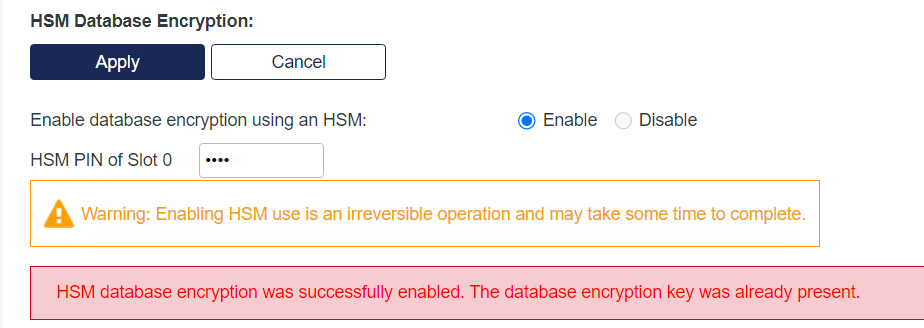
Select Enable database encryption using an HSM radio button, provide HSM PIN and then click Apply.
-
On clicking Apply, a key is generated automatically. If a key is already present in the HSM (or in the case of a PIN update), an appropriate message(s) is displayed.
If you want to create a key manually or edit its attributes, refer Manual Key Generation.
Enabling HSM (with the SAS solution) is a one-way, irreversible operation that cannot be undone.
SAS Site Import
If the HSM is enabled on the primary SAS server, and the administrator wants to import an SAS site on the secondary SAS server, the administrator must perform the following steps to setup the secondary SAS site with HSM integration:
-
Install the secondary SAS server.
-
Install Network HSM Access Provider and PTKC packages.
-
Export site information from the primary SAS server (already running the HSM integration).
-
Import the site information into the secondary SAS server.
-
Enter the HSM PIN.
-
Perform IISRESET operation.
Verify Encryption
To verify if the encryption is completed successfully, follow the steps below:
-
Create a new user (or update an existing user).
-
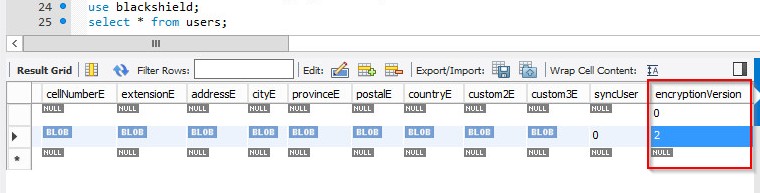
Check the value of the encryptionVersion column.
If the value of the encryptionVersion column is set to 2, it means that the encryption is achieved
successfully using the HSM.