Group Filtering
SafeNet Agent for Pluggable Authentication Module (PAM) provides group filtering capabilities to allow or ignore SafeNet multifactor authentication (MFA) for single or multiple local and domain groups. This enables targeted security without enforcing universal MFA, ensuring critical access protection while minimizing disruption. Follow the below configuration steps for applying SafeNet MFA after specifying the groups (local/domain).
Group filtering:
-
Apply MFA: Users in the specified groups will be prompted for SafeNet MFA. Users not belonging to any of the specified groups can login using their local or AD credentials.
-
Ignore MFA: Users in the specified groups will bypass SafeNet MFA, allowing users to login using only their local or AD/LDAP password. Users not belonging to any of the specified groups must use SafeNet MFA for access.
Capabilities
The group types that are supported by each group filtering configuration for Ubuntu and RHEL machines are displayed in the table that follows.
Up to 2 levels of nested groups are supported with SSSD. For example, group 2 can include group 1, which in turn can include a user.
In the case of local machines, follow the same general steps as domain-joined machines, but omit the step involving /etc/sssd/sssd.conf as it is not applicable for local group configurations.
| Group Filtering Configuration |
Condition | Domain or Local |
Single Group |
Multiple Groups |
Nested Groups |
|---|---|---|---|---|---|
Apply MFA |
use_fully_qualified_names = False |
Domain |
Yes |
Yes |
Yes |
use_fully_qualified_names = True |
Domain |
Yes |
No |
No |
|
N/A |
Local |
Yes |
Yes |
No |
|
Ignore MFA |
use_fully_qualified_names = False |
Domain |
Yes |
Yes |
Yes |
use_fully_qualified_names = True |
Domain |
Yes |
No |
No |
|
N/A |
Local |
Yes |
Yes |
No |
Limitations
- Multiple and nested group configurations are not supported when
use_fully_qualified_names = Trueis set in /etc/sssd/sssd.conf.
Ubuntu group filtering configurations
Apply MFA
This group filtering configuration supports two conditions.
Setting use_fully_qualified_names=False or True in the /etc/sssd/sssd.conf file controls whether domain names are excluded or included in usernames.
use_fully_qualified_names = False
To implement this condition:
-
Set
use_fully_qualified_names = Falsein /etc/sssd/sssd.conf.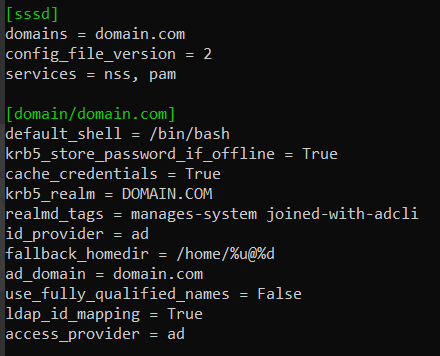
-
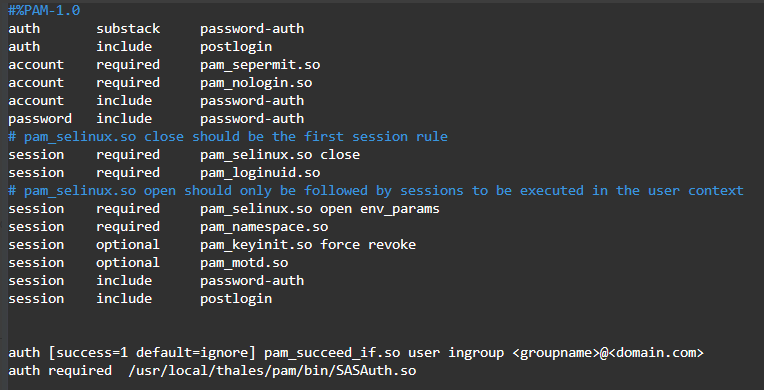
Add the following lines to either /etc/pam.d/sshd or /etc/pam.d/su.
-
For single and nested groups, add:
auth [success=ignore default=1] pam_succeed_if.so user ingroup <groupname>auth required /usr/local/thales/pam/bin/SASAuth.so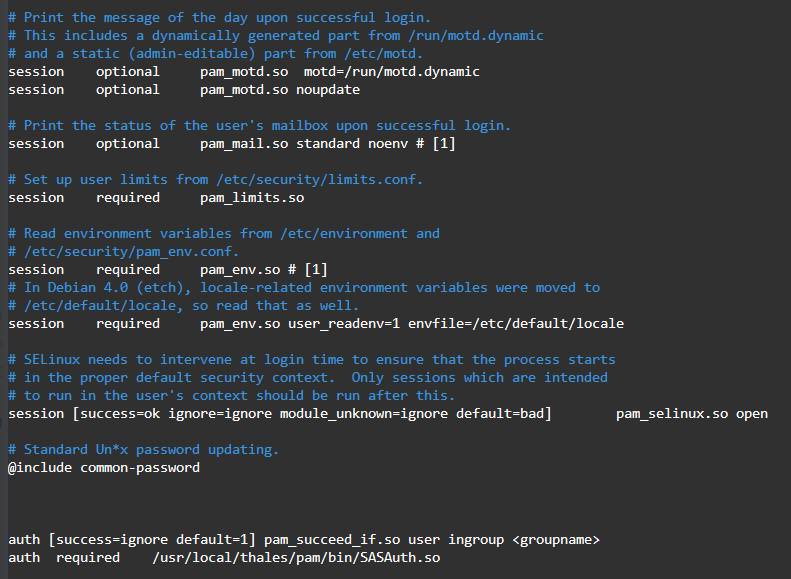
-
For multiple groups, add:
auth [success=ignore default=1] pam_succeed_if.so user ingroup <groupname1>auth required /usr/local/thales/pam/bin/SASAuth.soauth [success=ignore default=1] pam_succeed_if.so user ingroup <groupname2>auth required /usr/local/thales/pam/bin/SASAuth.so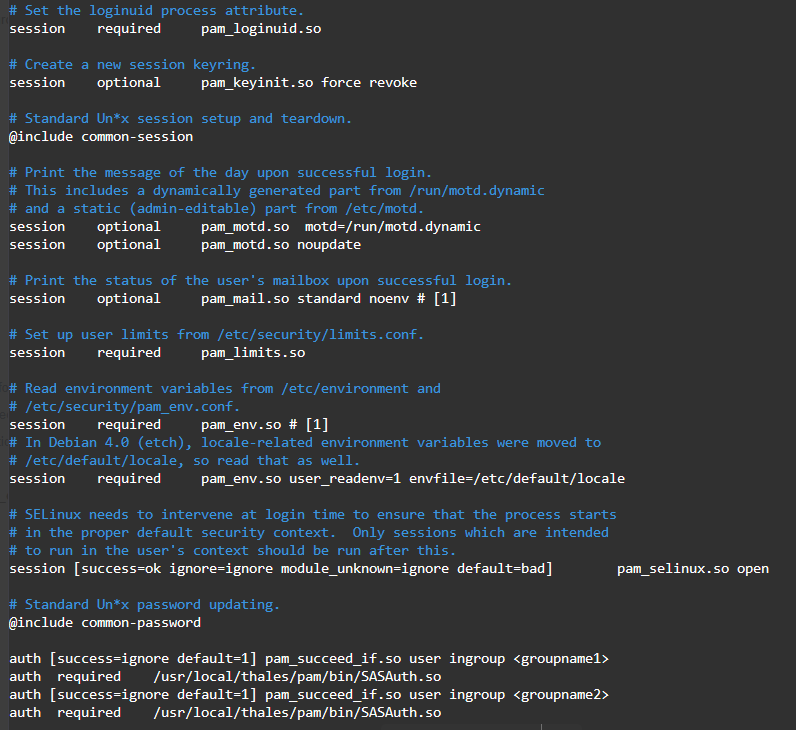
-
use_fully_qualified_names = True
To implement this condition:
-
Set
use_fully_qualified_names = Truein /etc/sssd/sssd.conf.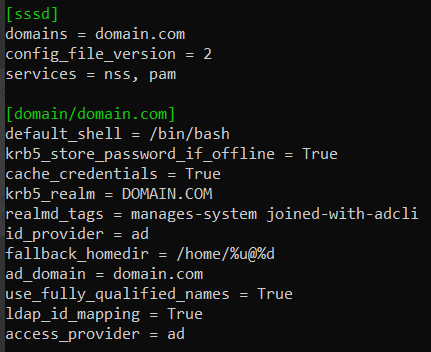
-
Add the following lines to either /etc/pam.d/sshd or /etc/pam.d/su.
For a single group only, add:
auth [success=ignore default=1] pam_succeed_if.so user ingroup <groupname>@domain.comauth required /usr/local/thales/pam/bin/SASAuth.so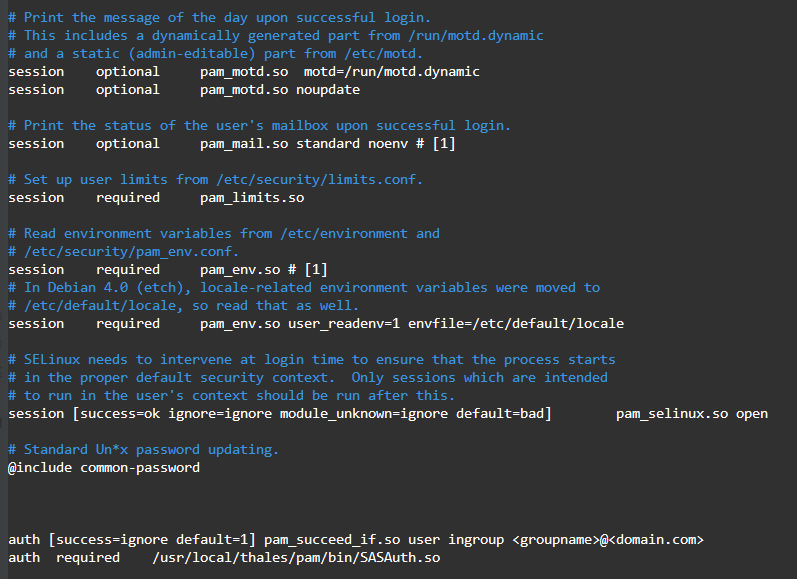
Ignore MFA
This group filtering configuration supports two conditions.
Setting use_fully_qualified_names=False or True in the /etc/sssd/sssd.conf file controls whether domain names are excluded or included in usernames.
use_fully_qualified_names = False
To implement this condition:
-
Set
use_fully_qualified_names = Falsein /etc/sssd/sssd.conf.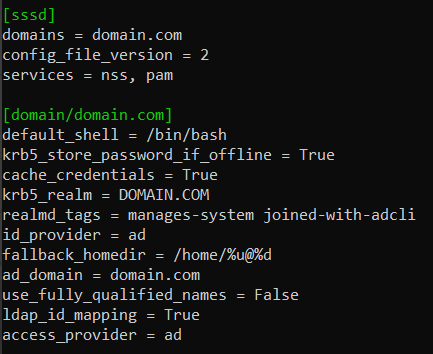
-
Add the following lines to either /etc/pam.d/sshd or /etc/pam.d/su.
-
For single and nested groups, add:
auth [success=1 default=ignore] pam_succeed_if.so user ingroup <groupname>auth required /usr/local/thales/pam/bin/SASAuth.so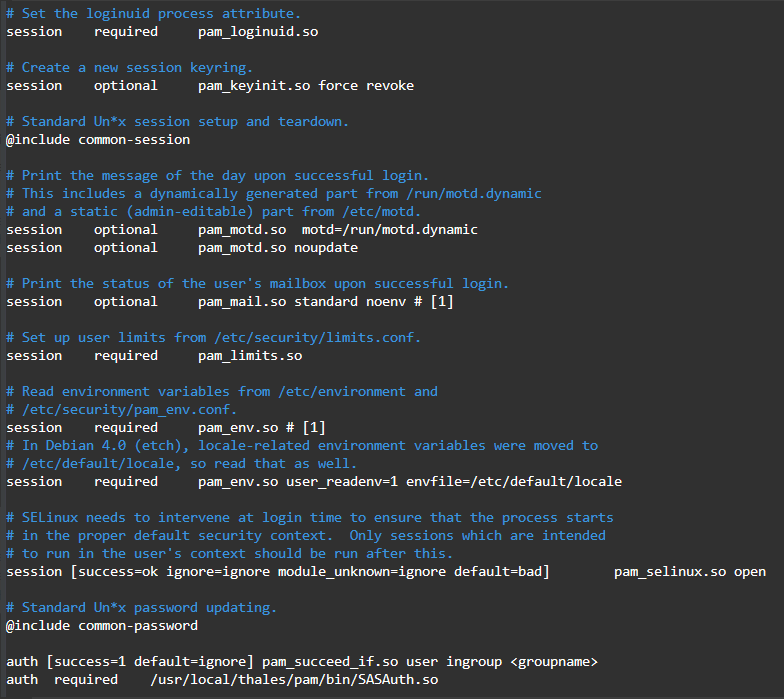
-
For multiple groups, add:
auth [success=2 default=ignore] pam_succeed_if.so user ingroup <groupname1>auth [success=1 default=ignore] pam_succeed_if.so user ingroup <groupname2>auth required /usr/local/thales/pam/bin/SASAuth.so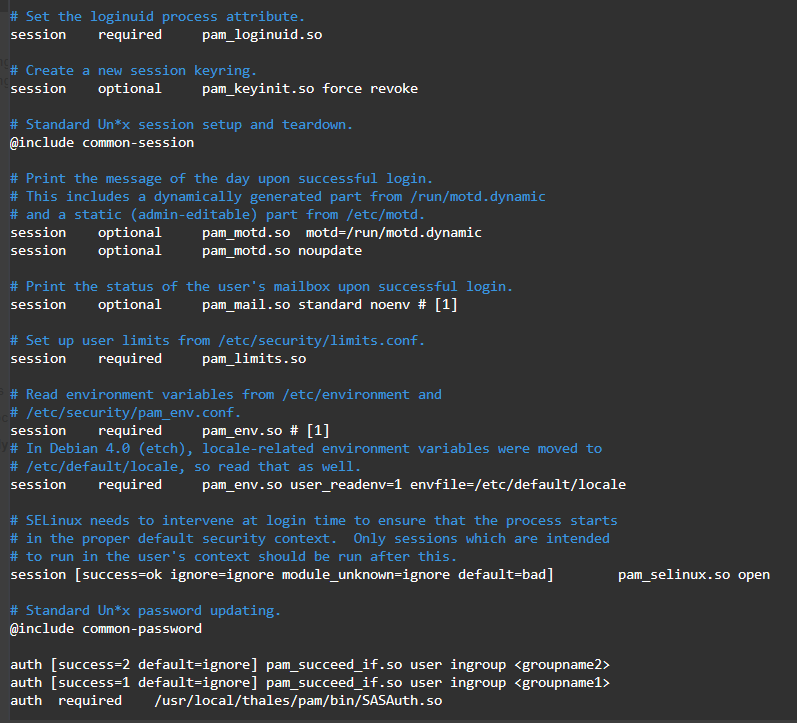
-
use_fully_qualified_names = True
To implement this condition:
-
Set
use_fully_qualified_names = Truein /etc/sssd/sssd.conf.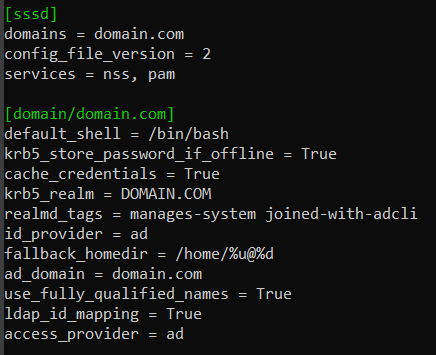
-
Add the following lines to either /etc/pam.d/sshd or /etc/pam.d/su.
For a single group only, add:
auth [success=1 default=ignore] pam_succeed_if.so user ingroup <groupname>@domain.comauth required /usr/local/thales/pam/bin/SASAuth.so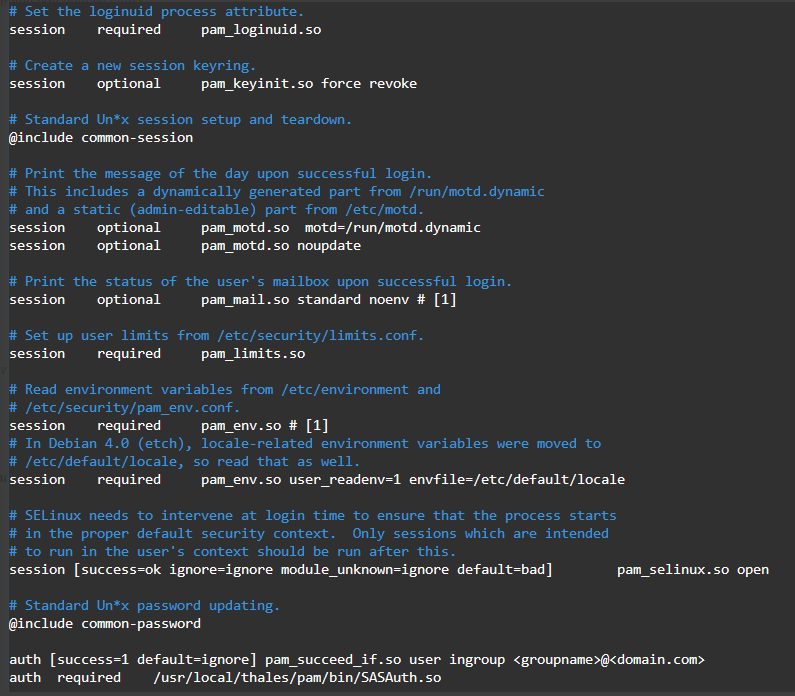
RHEL group filtering configurations
Apply MFA
This group filtering configuration supports two conditions.
Setting use_fully_qualified_names=False or True in the /etc/sssd/sssd.conf file controls whether domain names are excluded or included in usernames.
use_fully_qualified_names = False
To implement this condition:
-
Set
use_fully_qualified_names = Falsein /etc/sssd/sssd.conf.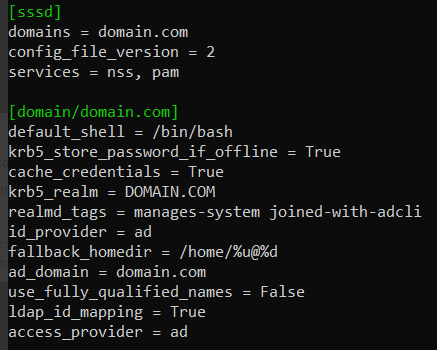
-
Add the following to either /etc/pam.d/sshd or /etc/pam.d/su.
-
For single and nested groups, add:
auth [success=1 default=ignore] pam_succeed_if.so user notingroup <groupname>auth required /usr/local/thales/pam/bin/SASAuth.so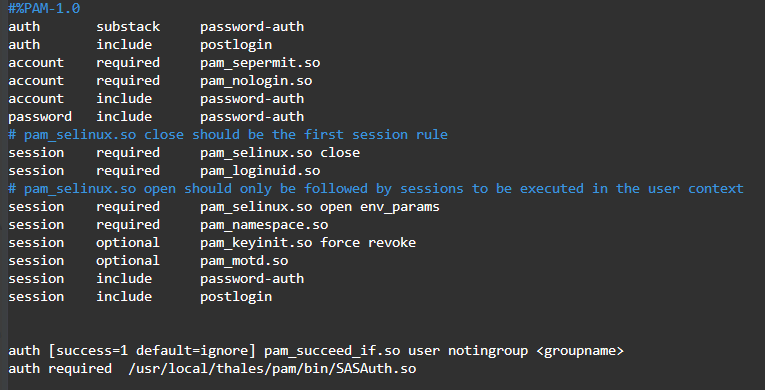
-
For multiple groups, add:
auth [success=1 default=ignore] pam_succeed_if.so user notingroup <groupname1>auth required /usr/local/thales/pam/bin/SASAuth.soauth [success=1 default=ignore] pam_succeed_if.so user notingroup <groupname2>auth required /usr/local/thales/pam/bin/SASAuth.so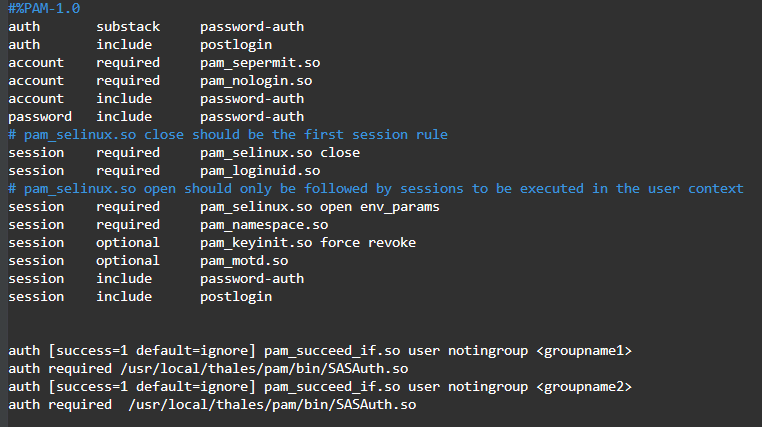
-
use_fully_qualified_names = True
To implement this condition:
-
Set
use_fully_qualified_names = Truein /etc/sssd/sssd.conf.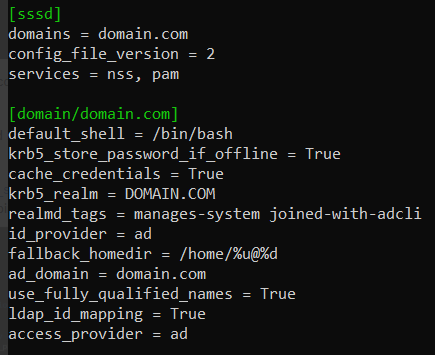
-
Add the following lines to either /etc/pam.d/sshd or /etc/pam.d/su.
For a single group only, add:
auth [success=1 default=ignore] pam_succeed_if.so user notingroup <groupname>@domain.com>auth required /usr/local/thales/pam/bin/SASAuth.so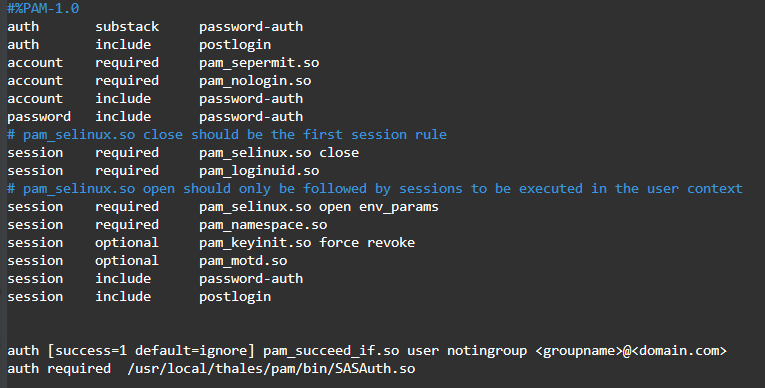
Ignore MFA
This group filtering configuration supports two conditions.
Setting use_fully_qualified_names=False or True in the /etc/sssd/sssd.conf file controls whether domain names are excluded or included in usernames.
use_fully_qualified_names = False
To implement this condition:
-
Set
use_fully_qualified_names = Falsein /etc/sssd/sssd.conf.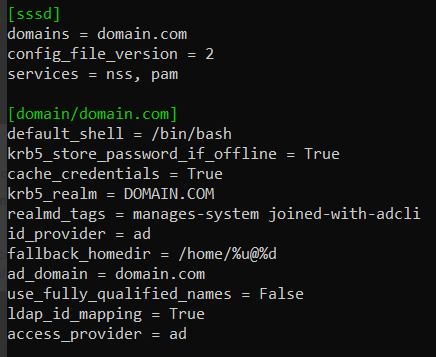
-
Add the following lines to either /etc/pam.d/sshd or /etc/pam.d/su.
-
For single and nested groups, add:
auth [success=1 default=ignore] pam_succeed_if.so user ingroup <groupname>auth required /usr/local/thales/pam/bin/SASAuth.so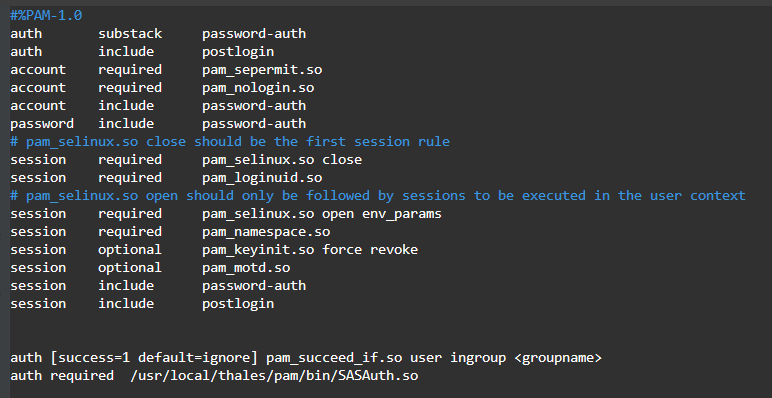
-
For multiple groups, add:
auth [success=2 default=ignore] pam_succeed_if.so user ingroup <groupname1>auth [success=1 default=ignore] pam_succeed_if.so user ingroup <groupname2auth required /usr/local/thales/pam/bin/SASAuth.so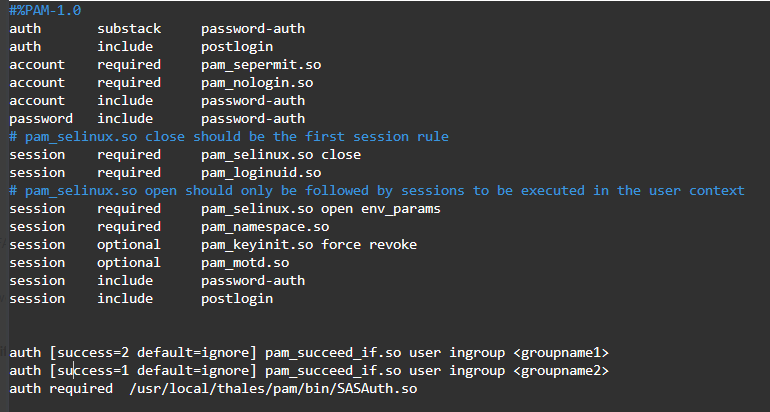
-
use_fully_qualified_names = True
To implement this condition:
-
Set
use_fully_qualified_names = Truein /etc/sssd/sssd.conf.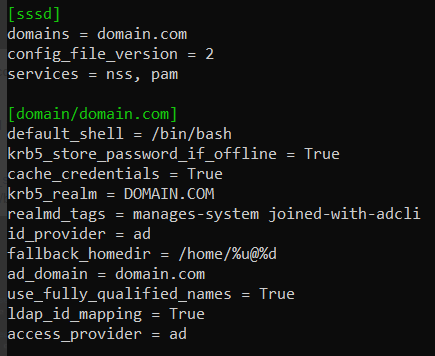
-
Add the following lines to either /etc/pam.d/sshd or /etc/pam.d/su.
For a single group only, add:
auth [success=1 default=ignore] pam_succeed_if.so user ingroup <groupname>@domain.comauth required /usr/local/thales/pam/bin/SASAuth.so