HashiCorp Vault
This document provides the necessary information to install, configure, and integrate HashiCorp Vault with the CipherTrust Manager.
A modern system requires access to a multitude of secrets: database credentials, API keys for external services, credentials for service-oriented architecture communication, and so on. Understanding who is accessing what secrets is already very difficult and platform-specific. Adding on key rolling, secure storage, and detailed audit logs is almost impossible without a custom solution.
HashiCorp Vault is a tool for securely accessing the secrets. A secret is anything that you want to tightly control access to, such as API keys, passwords, certificates, and more. HashiCorp Vault provides a unified interface to any secret while providing a tight access control and recording a detailed audit log.
Supported Product Versions
CipherTrust Manager
- CipherTrust Manager 2.11.1 LTS and higher
CipherTrust Application Data Protection (CADP)
- CADP for C v8.18.0 and higher (using underlying PKCS#11 provider)
HashiCorp Vault
- HashiCorp Vault 1.0.2 and higher
Supported Mechanism
- 0x01 CKM_RSA_PKCS (the only supported mechanism)
This integration is validated on Red Hat Enterprise Linux Server 64-bit.
Prerequisites
Ensure that HashiCorp Vault is installed and configured properly. Refer to the HashiCorp Vault documentation for details.
Ensure that CADP for C is installed and configured properly. Refer to the Quick Start for details.
Ensure that the CipherTrust Manager is installed and configured. Refer to the CipherTrust Manager documentation for details.
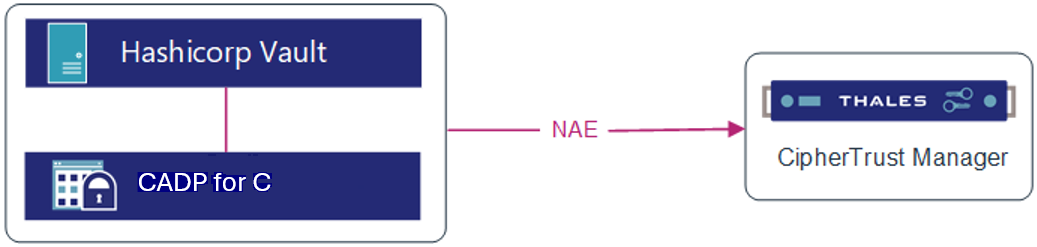
HashiCorp Vault communicates with the CipherTrust Manager using the Network Attached Encryption (NAE) Interface. Ensure that the NAE interface is configured. Refer to the CipherTrust Manager documentation for details.
Ensure that the port configured on NAE interface is accessible from the HashiCorp Vault machine.
Ensure that SSL is configured. Refer to Setting up SSL for details.

